Table of Contents
- Overview
- Key Terms and Acronyms
- Standard Threat Categories Used by Cisco Talos
- Cisco Firepower Configuration Elements (Sample)
- Cisco Talos Threat Intelligence Services Overview
- Sample List of Supported Protocols (Excerpt)
- Conclusion
Overview: Cisco Firepower & Cisco Talos Threat Intelligence
What Is It?
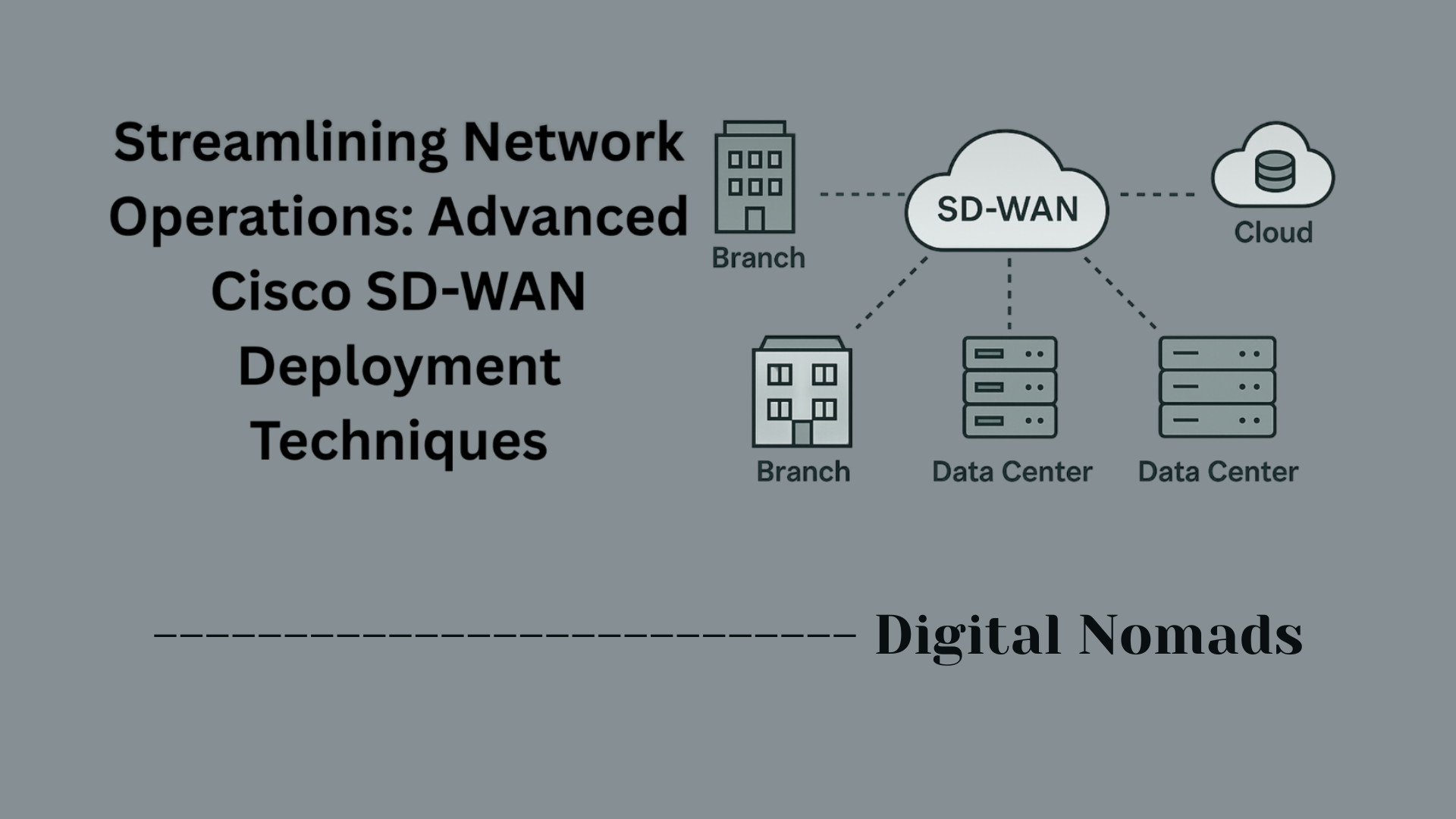
Cisco Firepower is Cisco’s next-generation firewall and security platform that provides advanced threat protection, detailed network visibility, and policy enforcement capabilities for organizations of all sizes. It includes features like intrusion prevention, application control, and malware defense to guard against a broad spectrum of cyber threats.
Cisco Talos Threat Intelligence is a globally recognized threat research and intelligence organization within Cisco. Talos analyzes massive amounts of security data to detect emerging threats, generate intelligence, and provide rapid, actionable protection updates. This intelligence feeds directly into Cisco’s security products—including Firepower—ensuring defenses are always up-to-date against the latest threats.
Why Do You Need to Know About It?
- Rising Cyber Threats: Organizations face constant threats like ransomware, phishing, advanced persistent threats (APTs), and zero-day exploits. Having real-time, actionable intelligence is crucial for defense.
- Automated Protection: With the integration of Talos threat intelligence, Cisco Firepower can automatically block connections to malicious sites, detect unknown malware, and rapidly respond to new attacks—minimizing manual effort and reaction time.
- Proactive Security Posture: Instead of waiting for threats to be discovered internally, organizations benefit from global threat research that anticipates emerging risks and adapts protections accordingly.
- Compliance & Visibility: Firepower provides robust reporting, policy enforcement, and audit tools to support regulatory compliance and internal security governance.
How Does It Work?
- Threat Intelligence Feeds: Talos continuously analyzes global security telemetry and delivers real-time updates (like malicious IPs, domains, file hashes, and attack signatures) directly to Cisco Firepower devices.
- Policy Enforcement: Firepower uses this intelligence to update security policies, enforce rules, and block traffic related to known threats—across both IT and OT (operational technology) environments.
- Layered Defense: Multiple security mechanisms—such as access control, intrusion prevention, malware protection, and network analytics—work together, leveraging Talos data to prevent, detect, and respond to attacks.
- Incident Response: When suspicious activity is detected, Firepower systems can automatically alert, quarantine, or block threats, providing quick containment and aiding in recovery.
In summary: Cisco Firepower with Talos Threat Intelligence provides a comprehensive, automated, and adaptive security solution, helping organizations stay ahead of sophisticated cyber adversaries and keep their networks, data, and operations safe.
Key Terms and Acronyms
Here are the most important terms and acronyms you’ll encounter when exploring Cisco Firepower and Cisco Talos Threat Intelligence:
- Cisco Firepower: Cisco’s next-generation firewall and intrusion prevention system that delivers advanced threat protection and deep network visibility.
- Cisco Talos: The global threat intelligence and research team at Cisco, responsible for detecting, analyzing, and disseminating information about emerging cybersecurity threats.
- Threat Intelligence: Context-rich data and analysis concerning cyber threats, threat actors, vulnerabilities, and attack methods.
- IoC (Indicator of Compromise): Evidence of a potential security incident, such as suspicious IP addresses, file hashes, domains, or network traffic anomalies.
- AMP (Advanced Malware Protection): Cisco’s security solution that leverages real-time threat intelligence to detect and block malware quickly.
- TTD (Time to Detect): The elapsed time between when a threat enters an environment and when it’s detected by security systems.
Standard Threat Categories Used by Cisco Talos
Cisco Talos organizes cyber threats into well-defined categories to help organizations understand risks and implement effective defenses. Here are the main threat categories tracked by Cisco Talos:
- Malware: Malicious software designed to disrupt, damage, or gain unauthorized access to computers, networks, or data. Examples include viruses, worms, ransomware, trojans, and spyware.
- Phishing: Deceptive techniques aimed at tricking individuals into disclosing sensitive information, such as login credentials or financial details, often via fraudulent emails or websites.
- Advanced Persistent Threat (APT): Sustained and targeted cyberattacks, typically orchestrated by well-funded and skilled adversaries, focused on stealing data or disrupting operations over extended periods.
- Botnet: A network of compromised computers and devices remotely controlled by malicious actors, often used to carry out coordinated attacks like DDoS or mass spam campaigns.
- Exploit: Code, scripts, or techniques that take advantage of vulnerabilities in systems or applications to facilitate unauthorized actions.
- Command and Control (C2): Communication channels used by attackers to maintain persistent control over compromised devices and manage malicious operations remotely.
Cisco Firepower Configuration Elements (Sample)
These are the core components you’ll typically configure when setting up Cisco Firepower to leverage Cisco Talos Threat Intelligence for advanced protection:
- Access Control Policies: Rules that determine what network traffic is permitted or denied. They act as the primary security gatekeepers, specifying which sources, destinations, and applications are allowed.
- Security Intelligence Feeds: Automated threat feeds—often powered by Cisco Talos—used to proactively block connections to known malicious IP addresses, domains, or URLs based on the latest threat research.
- Network Analysis Policies: Settings that control how network traffic is inspected for suspicious activities or threats. This includes traffic pre-processing and defining which protocols and file types get extra scrutiny.
- Device Management: The process of adding, configuring, and maintaining Firepower appliances and sensors. Enables centralized management, software updates, and continuous policy enforcement.
- Intrusion Policies: Rulesets that detect and block known and unknown attacks by inspecting network streams for exploit attempts and malicious payloads.
- Logging and Reporting: Configurable mechanisms to capture, store, and analyze security events. These help track incidents, demonstrate compliance, and improve overall security posture.
Cisco Talos Threat Intelligence Services Overview
Cisco Talos delivers world-class threat intelligence and security services designed to help organizations anticipate, detect, and respond to cyber threats more effectively. Here’s an overview of their core offerings:
- Comprehensive Threat Intelligence: Talos provides global, real-time insights into emerging threats—leveraging advanced AI and machine learning to process large datasets and deliver actionable intelligence across the Cisco security portfolio.
- Malware Defense: Multilayered protection that uses behavioral analysis, file reputation, and sandboxing to detect and block known and unknown malware, including zero-day threats.
- Email Security: Ray-layered protection that filters out malicious emails, prevents phishing, and blocks business email compromise attempts using sender reputation, URL scanning, and AI-based detection.
- Web Security: DNS and web filtering capabilities that block access to harmful domains and prevent malware downloads, phishing, and C2 communications at the network edge.
- Network Intrusion Prevention: Real-time detection and automated response to network-based attacks using deep packet inspection, signature-based, anomaly-based, and machine learning-driven threat detection.
- Incident Response & Proactive Services: Services that help organizations prepare for, investigate, and recover from cyber incidents. This includes creation of response playbooks, threat modeling, and direct support from experienced researchers and analysts.
- Integration & Automation: Threat intelligence is seamlessly integrated into Cisco’s security platforms, enabling automated defenses, rapid policy updates, and improved protection with less manual effort.
Together, these services empower organizations to stay ahead of evolving threats and optimize their security posture across endpoints, network, email, and cloud environments.
Sample List of Supported Protocols (Excerpt)
Cisco Firepower and Cisco Talos support deep inspection and enforcement for a wide range of common and specialized network protocols. Below is a sample list of the protocols commonly supported for network visibility, threat detection, and policy enforcement:
| Protocol | Protocol Number / Port | Description |
|---|---|---|
| TCP (Transmission Control Protocol) | 6 | Reliable, connection-oriented communications, widely used for applications like HTTP, FTP, SMTP. |
| UDP (User Datagram Protocol) | 17 | Unreliable, connectionless protocol for faster, lightweight communications, e.g., DNS, VoIP, streaming. |
| ICMP (Internet Control Message Protocol) | 1 | Used for network diagnostics and error reporting, such as ping and traceroute. |
| GRE (Generic Routing Encapsulation) | 47 | Tunneling protocol for encapsulating a wide variety of network layer protocols. |
| Modbus | 502/TCP | Protocol commonly used in industrial control systems for supervisory control and data acquisition (SCADA). |
| DNP3 | 20000/TCP | Distributed Network Protocol, also used in SCADA environments for communication between devices. |
| CIP (Common Industrial Protocol) | 44818/TCP | Industrial automation protocol frequently used for device communication on Ethernet/IP networks. |
| S7Commplus | 102/TCP | Protocol used for communication in Siemens industrial automation equipment. |
| HTTP/2, HTTP/3, QUIC | 80, 443, dynamic | Modern web protocols supported for application layer inspection and enforcement. |
| IEC 60870-5-104 | 2404/TCP | Protocol widely used in electrical engineering and energy automation (ICS/SCADA environments). |
Note: For comprehensive and up-to-date protocol support details, consult the official Cisco Firepower or Cisco Talos documentation for your specific product version.
Conclusion
Throughout this blog post, we’ve explored the powerful synergy between Cisco Firepower and Cisco Talos Threat Intelligence, and how together they provide comprehensive, real-time protection against today’s most dangerous cyber threats.
Key takeaways include:
- Cisco Firepower offers next-generation firewall capabilities, with deep visibility and automated threat response capabilities that adapt to your dynamic network needs.
- Cisco Talos is the brains behind Cisco’s security—delivering global, proactive threat intelligence that informs security policies, blocks emerging threats, and supports incident response.
- We broke down key terms and acronyms so that both beginners and seasoned security professionals can speak the same security language.
- We reviewed the standard threat categories Talos tracks—such as malware, phishing, APTs, botnets, and exploits—to better understand the nature of modern threats.
- We examined the core configuration elements of Firepower that enable effective policy enforcement, intrusion prevention, and visibility.
- We outlined Talos’s threat intelligence services and how they integrate seamlessly into Cisco’s security ecosystem to enable proactive defenses and rapid detection.
- Finally, we looked at a sample list of supported protocols, highlighting Cisco Firepower’s broad support for both IT and OT environments.
As cybersecurity threats grow more sophisticated, leveraging platforms like Cisco Firepower and threat intelligence from Talos can vastly improve your organization’s ability to defend, detect, respond, and recover from attacks.
Thanks for taking the time to read through this guide! If you have questions, want to explore deployment options, or see Cisco’s threat intelligence in action, reach out to your Cisco representative or visit Cisco Talos for more insights.
Stay secure, stay informed — and until next time, happy firewalling! 🔐🚀