Table of Contents
- Overview
- System Components
- Supported Deployment Modes
- Licensing and Smart Licensing
- Logging, Monitoring, and Integration
- Backup, Restore, and Upgrades
- Real-World Applications
- Specifications and Integration Details
- Conclusion
FirePOWER Threat Defense: Overview
What Is FirePOWER Threat Defense (FTD)?
FirePOWER Threat Defense (FTD) is a cybersecurity solution developed by Cisco that merges advanced firewall and threat prevention technologies into a unified security platform. It combines the next-generation firewall (NGFW) capabilities with threat intelligence, intrusion prevention, malware protection, and URL filtering. FTD aims to deliver integrated protection against a wide variety of network threats—both known and unknown—within a single, cohesive architecture.
Why You Need to Know About FirePOWER Threat Defense
- Comprehensive Security: FTD goes beyond traditional firewalling by incorporating real-time threat intelligence and multiple layers of defense, helping organizations safeguard against evolving cyber threats such as ransomware, phishing, and zero-day exploits.
- Visibility and Control: It provides deep visibility into network traffic, users, devices, and applications, enabling security teams to make informed decisions, enforce stringent policies, and respond quickly to incidents.
- Unified Management: With its centralized management options (such as Firepower Management Center or on-device Firepower Device Manager), FTD simplifies deployment, policy administration, and monitoring for organizations of all sizes.
- Regulatory Compliance: FTD helps businesses meet compliance requirements by offering robust logging, reporting, and audit capabilities for security events and policy changes.
- Scalability: Cisco offers FTD in hardware, virtual, and cloud form factors, allowing organizations to protect data centers, branch offices, and remote sites with a consistent security approach.
How FirePOWER Threat Defense Works
- Traffic Inspection: FTD inspects all incoming and outgoing traffic at various network layers using deep packet inspection, intrusion prevention signatures, file analysis, and reputation checks.
- Policy Enforcement: Security rules and policies are applied based on user identity, applications, content, and source/destination characteristics, providing granular access control.
- Threat Detection and Blocking: Advanced threat intelligence, integrated from Cisco Talos, powers real-time detection and blocking of known viruses, malware, exploits, and suspicious traffic. The solution also includes advanced malware protection to track and analyze files even after they have entered the network.
- Integration and Automation: Integration with third-party security tools and SIEMs via APIs and syslog, combined with automation features, streamlines incident response and enhances overall security posture.
- Continuous Monitoring: FTD generates alerts, logs, and reports for ongoing visibility into security events, enabling rapid detection and investigation of threats.
FirePOWER Threat Defense is designed for organizations that require a robust, flexible, and manageable defense system to safeguard their networks from increasingly sophisticated cyber threats. Its comprehensive toolset ensures proactive threat hunting, responsive controls, and ongoing protection in a dynamic digital landscape.
System Components of FirePOWER Threat Defense
These are the core elements that make up Cisco FirePOWER Threat Defense (FTD), providing comprehensive security through integrated management, control, and threat prevention:
- Firepower Threat Defense (FTD) Software: The unified software image that consolidates next-generation firewall (NGFW) capabilities, intrusion prevention, advanced malware protection, URL filtering, and network visibility into a single solution.
- Firepower Management Center (FMC): The centralized platform for managing multiple FTD devices. FMC offers holistic policy configuration, real-time event monitoring, detailed reporting, orchestration, and automation.
- Firepower Device Manager (FDM): The lightweight, on-box web-based management tool for configuring and managing individual FirePOWER appliances. Suitable for smaller deployments or single-device setups.
- Security Intelligence & Feeds: Provides up-to-date threat intelligence from Cisco Talos, including indicators of compromise, IP/domain reputation, URL categorization, and threat signature updates.
- Integration APIs & Connectors: RESTful APIs and built-in connectors enable integration with other security tools, SIEM platforms, and orchestration systems for enhanced automation, event forwarding, and ecosystem interoperability.
Supported Deployment Modes of FirePOWER Threat Defense
FirePOWER Threat Defense (FTD) offers flexible deployment modes to suit various network environments and security requirements. Here are the major supported modes, each providing distinct ways to inspect, control, and secure network traffic:
- Routed Mode: FTD acts as a traditional Layer 3 firewall, routing traffic between different network segments. This mode supports features like NAT, dynamic routing, and granular security policies. It is the most common deployment for creating clear network boundaries and inspection points.
- Transparent Mode: In this Layer 2, “bump-in-the-wire” deployment, FTD operates without altering IP addresses or network topology. The firewall bridges traffic between interfaces, providing security enforcement with minimal network changes—ideal for seamless integration into existing infrastructures.
- Inline Mode (Active/Fail-Open): FTD is inserted directly in the traffic path and actively inspects and enforces policies on live traffic. Inline configurations can also support fail-open operation to maintain business continuity in case of hardware or software failures.
- Passive Mode: FTD monitors traffic via SPAN or TAP ports without altering, blocking, or impacting packets. This mode is valuable for incident detection, security analytics, and environments where network disruption is not tolerated.
Each deployment mode allows organizations to align security controls with operational needs, ensuring scalable protection across data centers, branch offices, and remote sites.
Licensing and Smart Licensing for FirePOWER Threat Defense
Licensing in Cisco FirePOWER Threat Defense (FTD) is designed to be flexible, scalable, and easy to manage. The core model is built around Cisco’s Smart Licensing system, which streamlines how organizations acquire, assign, and monitor licenses across devices and features.
- Base License (Included): Every FTD appliance comes with a base license that grants essential firewall features like application visibility, user awareness, network address translation (NAT), routing, and VPN capabilities. The base license is perpetual and does not expire[5][10].
-
Subscription-Based Advanced Licenses:
For next-generation features, FTD offers optional term-based (1, 3, or 5 years) licenses. Key subscriptions include:
- Threat (T): Enables Intrusion Prevention System (IPS) for advanced protection against network attacks.
- Malware (M): Activates Advanced Malware Protection (AMP) for file inspection and blocking malware threats.
- URL (C): Adds URL filtering based on category and reputation to control web access.
-
Smart Licensing Portal:
All license management occurs through Cisco’s centralized Smart Licensing portal. Administrators can:
- Activate licenses without product activation keys (no PAKs required).
- View and manage license pools organization-wide.
- Transfer licenses flexibly between devices, ensuring efficient use of purchased subscriptions[1][5].
- Flexible Feature Activation: Licenses are not hardware-locked; features can be activated or deactivated on demand through FMC or FDM, based on operational or compliance needs. Organizations can start with basic features and add advanced security as threats evolve.
- High Availability and Clustering: In HA or cluster deployments, each device requires its own matching feature licenses. Licenses can be reassigned, but every participating appliance must be properly licensed for unified operation[5].
Smart Licensing helps ensure compliance, simplifies upgrades, and allows organizations to adapt licensing as their security requirements grow.
Logging, Monitoring, and Integration in FirePOWER Threat Defense
Cisco FirePOWER Threat Defense (FTD) provides robust logging, real-time monitoring, and deep integration capabilities to help organizations detect, investigate, and automate responses to threats.
- Event Logging and Syslog Export: FTD records a wide variety of security events such as connection attempts, intrusion detections, malware activity, user access, and policy changes. Logs are customizable by event type, severity, and destination. Administrators can export logs to external SIEMs or log management solutions via syslog, with support for filtering, custom event lists, adjustable logging levels, and rate limits to control message volume[1][5][8].
- Real-Time Monitoring: The Firepower Management Center (FMC) and Firepower Device Manager (FDM) both provide dashboards, event viewers, and alerting systems for live monitoring. These dashboards present visual analytics, traffic statistics, detected threats, and device health. FMC also supports cloud integrations for extended analytics, such as Cisco Threat Response[11][12].
- Alerting and Automation: Administrators can set up alerting rules for specific security events—such as intrusion attempts, malware detections, or system issues—then receive notifications via email, syslog, or other channels. Integration with automation platforms allows for faster incident response.
- APIs and Third-Party Integration: FTD exposes RESTful APIs as well as SNMP, enabling integration with external security, automation, and monitoring platforms. Organizations use these to automate repetitive tasks, ingest vulnerability data, or orchestrate complex response workflows. Popular integrations include Splunk, Tenable, IBM QRadar, LogicMonitor, and Securonix[6][10][11][13].
- Log Event Types: Common event types include connection events, file and malware detections, intrusion activity, policy compliance, and device health. These are mapped to parsed metadata for easy correlation and alerting in SIEM tools[8][11].
Collectively, these features give security teams full visibility into network activity, support compliance requirements, and enable rapid threat containment through automation and analytics.
Backup, Restore, and Upgrades in FirePOWER Threat Defense
Maintaining resilience and up-to-date protection in Cisco FirePOWER Threat Defense (FTD) relies on proper backup, restore, and upgrade procedures. Here’s how each process works and what administrators should know:
- Backup: FTD supports scheduled or manual configuration-only backups via the Firepower Management Center (FMC) or Firepower Device Manager (FDM). Best practices include saving backups to a secure external location, backing up devices regularly, before upgrades, and after configuration changes[1][7]. In high-availability (HA) or cluster setups, backup each device individually, as each backup is unique to the device’s role[7].
-
Restore:
Restoring from backup replaces configuration data with settings from the backup file, prompting an automatic device reboot. Restore operations are performed from the device’s management portal (FMC or FDM) or the device CLI. In HA or clustered deployments, restore only one peer or node at a time, always using its specific backup file; do not restore the same file to multiple appliances[5][7].
- VPN certificates and some event data are not restored and may require reconfiguration after restore[10].
- The management IP address is preserved during restore, aiding in device recovery across different networks[5].
-
Upgrade:
Upgrades are performed through FMC or FDM. The upgrade process involves uploading the new software package, running pre-checks, and applying the update. It's critical to back up both the FTD appliance and the management center before starting an upgrade. Upgrades cause a device reboot, so schedule during maintenance windows to minimize disruption[8][11][12].
- Always upgrade the management center first, followed by managed devices[8][12].
- Use the system’s upgrade wizard or system updates page for guidance, rollback options, and monitoring progress[8][15].
- In HA/clustered setups, upgrade peers or nodes sequentially, not simultaneously[7][15].
-
Best Practices:
- Store backup files securely, as they are unencrypted archives containing configuration and key data[7][10].
- Perform restores and upgrades during planned outages or low-usage windows.
- After any recovery or upgrade, verify system functionality and redeploy new configurations as needed[11][12].
- Maintain documented backup and upgrade procedures as part of your organization's disaster recovery plan[7].
Following disciplined backup, restore, and upgrade routines ensures business continuity and keeps your network security posture current.
Real-World Applications of FirePOWER Threat Defense
Cisco FirePOWER Threat Defense (FTD) is utilized by organizations across industries to address modern cybersecurity challenges in diverse network environments. Below are some common real-world applications where FTD plays a critical role:
- Enterprise Perimeter Defense: FTD deploys advanced threat prevention at the network edge, blocking intrusions, ransomware, and phishing attacks before they reach internal systems. It leverages indicators of compromise from Cisco Talos to identify active threats and eliminate malicious traffic in real time[1][3].
- Data Center Security: High-performance FirePOWER appliances protect sensitive workloads by segmenting data center traffic, monitoring east-west flows, and providing deep packet inspection. FTD supports SSL/TLS decryption to detect threats hidden in encrypted sessions, safeguarding mission-critical assets[2][7].
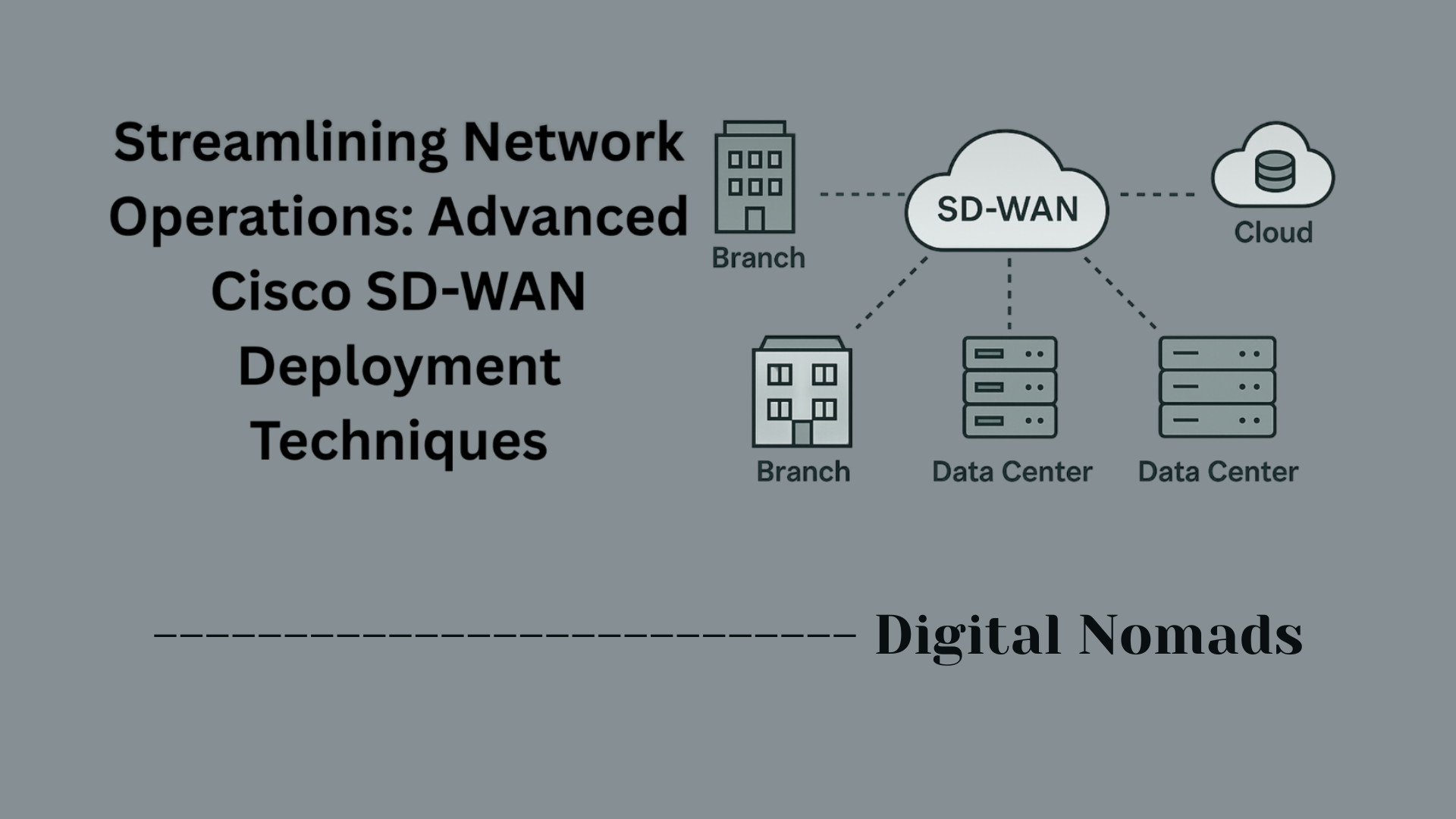
- Branch Office and SD-WAN Integration: FTD enables secure connectivity for distributed branches via SD-WAN, providing consistent security policies, VPN support, and dynamic routing. It protects remote sites from internet-based threats and ensures compliance across the organization[1][12].
- Cloud and Hybrid Environments: FirePOWER Threat Defense Virtual (FTDv) extends security controls to cloud platforms (AWS, Azure, VMware, KVM), offering organizations advanced threat protection and policy enforcement regardless of deployment location[9][10].
- Compliance and Regulatory Enforcement: Industries subject to standards like PCI-DSS, HIPAA, or GDPR use FTD’s granular logging, policy enforcement, and reporting features to meet compliance requirements and demonstrate audit readiness[8][11].
- Integration with Security Analytics Platforms: FTD’s comprehensive event telemetry can be integrated with SIEM and analytics platforms (such as Splunk, IBM QRadar, Microsoft Sentinel), enabling advanced incident detection, rapid investigation, and automated response[6][17].
- Application and User Control: Organizations leverage FTD to define and enforce acceptable use policies, manage application access, and monitor user activity, reducing insider risk and limiting exposure to shadow IT[12][18].
- Zero Trust Architectures: FTD is often deployed as part of a zero trust security model, providing micro-segmentation, identity-based access control, and continuous monitoring to limit lateral movement and strengthen overall network defense[1].
These applications demonstrate the versatility of FirePOWER Threat Defense in meeting security challenges across perimeter, data center, branch, cloud, and compliance-focused deployments.
Specifications and Integration Details of FirePOWER Threat Defense
Below are the key specifications and integration capabilities you need to know about Cisco FirePOWER Threat Defense (FTD).
- Supported Versions: FTD supports a variety of versions; commonly referenced versions include Firepower Device Manager (FDM) 6.7+, Firepower Management Center (FMC) 6.1+, and Threat Defense images such as 6.3, 6.6, and later releases (up to 7.x in latest compatibility guides)[3][7][12].
- Hardware and Virtual Compatibility: Supported on dedicated appliances (e.g., Firepower 1000, 2100, 4100, 9300 Series) and as a virtual appliance for VMware, KVM, AWS, and Azure cloud deployments[1][11][16].
-
Core Protocols and Event Formats:
- Syslog (including CSV and Name-Value Pair): Used for event export and SIEM integration[3][13].
- REST API & SNMP (v1, 2c, 3): Enables automation, monitoring, and external tool integration. SNMPv3 is recommended for secure monitoring[10][12].
- Supported Event Types: Intrusion, connection, audit, malware, user access, policy change, system health events[3][8].
-
Throughput and Performance:
- Varies by model: ranges from ~890 Mbps to 5+ Gbps in the 1000 Series to 30+ Gbps in highest-end appliances (see model-specific data sheets)[1][5][11].
- Maximum DDoS prevention rates and concurrent session limits scale with hardware; refer to hardware guides for details[4][5].
-
Integration and Extensibility:
- SIEM/Analytics: Integrates with IBM QRadar, Splunk, Cisco XDR, Netsurion XDR, and cloud SIEMs for log ingestion, threat detection, and reporting[8][9][15][17].
- Orchestration/Monitoring: Supports event forwarding, automated incident response, and integration with solutions like Tenable, LogicMonitor, and Cisco Threat Response[5][6][15].
- APIs and Connectors: RESTful APIs allow custom integration and automation with both Cisco and third-party tools[12][15].
- Discovery and Identity Integration: FTD can automatically discover network devices and user identities, offering enhanced logging and access control granularity[3][12].
- Documentation and Support: Extensive administration, configuration, and integration guides are provided by Cisco for continued reference and to ensure compatibility across deployment types[7][12][15].
| Specification | Detail |
|---|---|
| Supported Versions | FDM 6.7+, FMC 6.1+, FTD 6.3+, Up to 7.x[3][7][12] |
| Supported Protocols | Syslog, REST API, SNMP v1/v2c/v3[3][10][12] |
| Event Formats | Syslog, CSV, Name-Value Pair[3][13] |
| Main Integration Targets | SIEMs (IBM QRadar, Splunk, Netsurion XDR), Cisco XDR, Security Analytics & Logging, Threat Intelligence Feeds[6][8][9][15] |
| Use Case Discovery | Automatic event and identity discovery[3][12] |
| Performance Range | ~890 Mbps – 54 Gbps depending on appliance[1][5][11] |
| Cloud and Virtual Support | VMware, KVM, AWS, Azure (virtual FTDv)[11][12] |
These specifications and integration features enable Cisco FirePOWER Threat Defense to fit into modern, hybrid cloud, and on-premises security environments, streamline threat visibility, and automate cyber defense workflows.
Conclusion
Throughout this blog post, we’ve explored the extensive capabilities and practical uses of Cisco FirePOWER Threat Defense (FTD) — a unified security solution designed to protect modern networks from today’s rapidly evolving cyber threats.
Here are some key takeaways:
- What It Is: FirePOWER Threat Defense combines next-generation firewall capabilities, intrusion prevention, advanced malware protection, and URL filtering into a single, integrated platform.
- Core Components: The solution is powered by modular components like FTD software, Firepower Management Center (FMC), and Firepower Device Manager (FDM), making it scalable for organizations of all sizes.
- Flexible Deployment: Whether in routed, transparent, inline, or passive mode, FTD adapts to diverse network architectures including on-premises, cloud, or hybrid.
- Licensing Made Easy: With Cisco Smart Licensing, organizations enjoy centralized, flexible, and on-demand licensing models that simplify feature management and compliance.
- Robust Monitoring & Integration: FTD provides rich logging, real-time dashboards, and seamless integration with SIEM and security platforms, allowing security teams to detect, respond, and automate actions against threats.
- Ongoing Management: Backups, upgrades, and restores are streamlined for business continuity and resilience, supported by best practices and documentation.
- Real-World Impact: From data center defense to securing remote branches and cloud-based assets, FirePOWER delivers protection across industries and infrastructure types.
In short, Cisco’s FirePOWER Threat Defense is a resilient, smart, and adaptable solution for enterprises looking to strengthen their cybersecurity stack while maintaining visibility and control across their environments.
Thanks for following along! Whether you're a network engineer, IT administrator, or security analyst, we hope this post helped demystify FirePOWER Threat Defense and gave you the insight needed to leverage it more effectively. Stay safe, stay secure — and keep defending what matters most. 🔒🔥
Until next time! 👋💻