Table of Contents
- Overview
- Interface Types
- Key Configuration Steps
- Common Interface Commands
- CLI Modes Overview
- Notable Notes
- Troubleshooting Tips
- Conclusion
Cisco Firepower Interface: Overview
Cisco Firepower interfaces are the connection points on Cisco Firepower Threat Defense (FTD) appliances, enabling the device to integrate securely and efficiently into your network environment. These interfaces are essential for data flow, device management, segmentation, and security policy enforcement.
What Is a Cisco Firepower Interface?
A Cisco Firepower interface is a logical or physical network port on a Cisco Firepower appliance, such as Firepower Threat Defense (FTD) or Firepower NGFW. These interfaces can be:
- Physical ports directly connected to your network cables.
- Logical subinterfaces (VLANs, bridge groups, or EtherChannels) that allow for more complex configurations and segmentation.
- Management interfaces dedicated to device administration, monitoring, and integration with tools like Firepower Management Center (FMC).
The interfaces are where the firewall inspects, routes, or bridges incoming and outgoing network traffic.
Why Should You Care About Firepower Interfaces?
Understanding and controlling Firepower interfaces is crucial for several reasons:
- Segmentation and Security: Interfaces define network boundaries, enabling you to enforce policies between different zones (e.g., inside, outside, DMZ).
- Efficient Traffic Management: Correct configuration supports redundancy, high availability, and optimal bandwidth usage.
- Device Management: A dedicated management interface ensures secure configuration, monitoring, and troubleshooting without interfering with data traffic.
- Scalability and Flexibility: Logical interfaces (like VLAN subinterfaces and port-channels) allow you to accommodate network growth and evolving security needs without new hardware.
- Regulatory Compliance: Proper isolation and auditability of network segments hinge on correct interface configuration.
In short, the way you configure Firepower interfaces determines how your network's security and functionality operate.
How Do Cisco Firepower Interfaces Work?
- Traffic Inspection: Interfaces are assigned roles and security policies in Firepower Management Center or Device Manager. As traffic enters or leaves the appliance, interfaces apply these rules—blocking, permitting, or inspecting packets as defined.
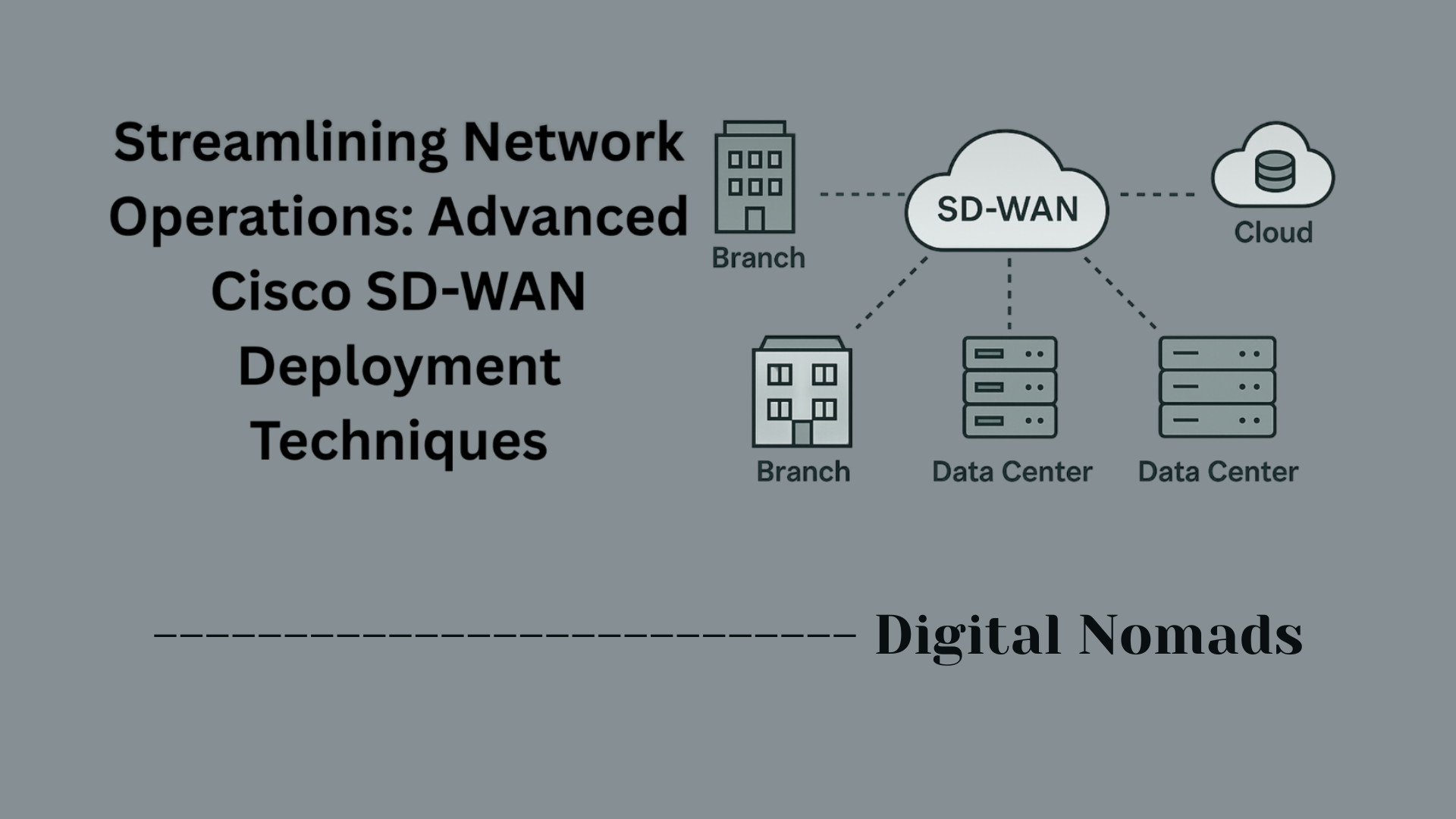
- Modes of Operation: Firepower devices support routed mode (Layer 3), transparent mode (Layer 2), and hybrid deployments. Interface types (physical, VLAN, bridge, etc.) adapt to these operational needs.
- Management & Monitoring: The management interface is isolated from data interfaces, safeguarding administrative access and facilitating centralized control from tools like FMC.
- Redundancy and Aggregation: Interfaces can be logically grouped (EtherChannel/port-channels), letting multiple connections act as one for greater bandwidth and failover protection.
- Flexibility: With support for subinterfaces, bridge groups, and port-channels, Firepower can fit a wide range of network designs, from simple perimeter firewalls to complex multi-segmented architectures.
Summary: Cisco Firepower interfaces are the foundation of the device’s security, connectivity, and management capabilities. Knowing how they work empowers you to design, configure, and troubleshoot robust security solutions tailored to your organization’s needs.
Interface Types
The Cisco Firepower platform supports several interface types, each tailored for specific network deployment needs. Understanding these types is essential for proper configuration and segmentation:
- Physical Interfaces: These are the foundational hardware ports on the device. Physical interfaces can be individually configured and are used to connect network segments directly. They support enabling/disabling, naming, and assignment of IP addresses.
- Bridge Group Interfaces: Bridge groups combine one or more interfaces into a single logical broadcast domain. Deploying bridge group interfaces in transparent mode enables the device to function as a Layer 2 firewall, passing traffic between segments as if they were on the same network, while still providing inspection.
- EtherChannel Interfaces (Port-Channels): EtherChannels, also known as port-channels, aggregate multiple physical interfaces into a single logical link. This provides redundancy and increased bandwidth. All member interfaces must share the same settings (type, speed, duplex).
- VLAN Subinterfaces: VLAN subinterfaces are logical interfaces that use IEEE 802.1Q tagging to segregate traffic on a single physical interface. Each subinterface is assigned a VLAN ID (1-4094) and can have independent security policies and IP configurations.
- Management Interface: The dedicated management interface is exclusively for device administration and communication with Firepower Management Center (FMC). It has its own IP address and supports static routing. This interface is required for initial setup and registration to FMC.
Key Configuration Steps
To successfully configure interfaces on Cisco Firepower, follow these step-by-step instructions:
-
Enable the Interface:
All physical and logical interfaces are disabled by default (except for the Diagnostic interface). Use the Firepower Device Manager (FDM), Firepower Management Center (FMC), or CLI to enable the required interface. -
Assign a Name and Description:
Interfaces must have a name before they can pass traffic. You can also set an optional description (up to 200 characters) to clarify the interface’s purpose or role. -
Configure Speed and Duplex Settings:
Set the duplex and speed based on your network needs and the connected hardware. Options typically include Auto, 10, 100, or 1000 Mbps. -
Set an IP Address:
Assign an IPv4 or IPv6 address to the interface (or VLAN subinterface). For VLAN subinterfaces, specify the VLAN ID (1–4094) and configure the unique IP addressing. -
Deploy Configuration Changes:
All configuration changes must be deployed before they become active. Using FMC or FDM, review your changes and deploy them to enforce configuration across the device.
Tip: Always confirm that your changes are successfully deployed, as interfaces remain inactive until the deployment is complete.
Common Interface Commands
Managing Cisco Firepower interfaces often requires using the command-line interface (CLI) for detailed status, troubleshooting, or for making changes that are not available in the graphical interface. Below are essential interface-related CLI commands, their syntax, and usage notes:
| Command | Description | Usage Example |
|---|---|---|
show interface |
Displays detailed status and configuration for all interfaces, including operational state, speed, and duplex settings. | show interface |
show interface ip brief |
Summarizes interface status and assigned IP addresses for quick overview and health checks. | show interface ip brief |
configure network |
Configures the management interface network settings such as IP address, subnet, and gateway. | configure network ipv4 manual 192.168.1.10 255.255.255.0 192.168.1.1 |
configure firewall |
Sets the device mode to routed or transparent, affecting how interfaces handle traffic. | configure firewall routed |
show route |
Shows the routing table, verifying how traffic will exit interfaces based on destination. | show route |
show running-config |
Displays the current active configuration, including all interface settings and policies. | show running-config |
configure manager add <FMC-IP> <key> |
Registers the device with Firepower Management Center (FMC) for central management. | configure manager add 192.168.0.5 mySecretKey |
show nameif |
Lists logical interface names (nameif) for easier identification within policies and logs. | show nameif |
Tip: To view supported command syntax or to troubleshoot a specific interface, use ? after the command or refer to the official command reference documentation.
CLI Modes Overview
The Cisco Firepower Threat Defense (FTD) device offers a hierarchical command-line interface (CLI), where each mode gives access to different sets of commands. Understanding these CLI modes is essential for proper configuration, monitoring, and troubleshooting:
-
User EXEC Mode:
The default login mode, allowing basic network status checks and monitoring such as viewing interface status. The prompt typically ends with>.
Example:show version -
Privileged EXEC Mode:
Accessed by enteringenable. This mode allows more advanced monitoring, troubleshooting, and some configuration capabilities. The prompt ends with#.
Example:show running-config -
Global Configuration Mode:
Accessed from Privileged EXEC withconfigure terminal. Allows system-level and interface configuration changes.
Example:interface GigabitEthernet1/1 -
Expert Mode:
For advanced troubleshooting or when underlying Linux access is required, enterexpertfrom Privileged EXEC. Use with caution, as this exposes the Linux shell and deeper system files.
Example:expert
Tip: Each mode restricts access to certain commands for user safety and system integrity. Always use the minimum-privilege mode needed for your task, and only enter Expert Mode when absolutely necessary.
Notable Notes
Here are important considerations and best practices to keep in mind when working with interfaces on Cisco Firepower appliances:
-
Management Interface:
The management interface is distinct from data interfaces and is crucial for device registration and initial setup. Only the management interface can be used for Firepower Management Center (FMC) communication, and it uses its own IP addressing and static routing.
Tip: Changes made to management settings after registration may need to be synchronized in FMC for them to take effect. -
VLAN Subinterfaces:
Each VLAN subinterface supports VLAN IDs from 1 to 4094, providing segmentation for different networks over a single physical link. Assigning the correct VLAN ID and IP addressing is essential for network separation and policy enforcement. -
Deployment Requirement:
After making interface configuration changes, you must deploy the changes from Firepower Management Center for them to become active. Failing to deploy will leave changed interfaces in an inactive or inconsistent state. -
Access Methods:
SSH and console access permissions may vary based on the hardware platform and configured user accounts. Always verify access method availability, especially after changes or upgrades. -
Physical and Logical Redundancy:
Redundant interface pairs can be set up for high availability. Only interfaces of the same physical type (e.g., both GigabitEthernet) can be paired. On supported platforms, you can configure up to 8 pairs, but not all models support this feature[2]. -
EtherChannel and Inline Sets:
Interfaces aggregated into an EtherChannel must have matching type and speed. For inline sets (used for transparent monitoring or IPS-only modes), configuration differs and may not support normal firewall functions[2]. -
Bridge Groups and Modes:
Interfaces can be organized into bridge groups for Layer 2 transparent mode, but each bridge group remains isolated from others. In routed mode, routing between interfaces is enabled[2]. -
Software Version Impact:
Certain interface features (such as auto-negotiation, inline sets, or offload/IPsec enhancements) may only be available on specific Firepower OS versions and hardware models. Always consult relevant release notes when planning an upgrade or feature implementation[5].
Reminder: Always confirm hardware model capabilities and supported configurations before making interface changes. Refer to the latest Cisco documentation and your platform’s release notes for updated capabilities and restrictions.
Troubleshooting Tips
Proper troubleshooting of Cisco Firepower interfaces involves a systematic approach. Use the following step-by-step recommendations to diagnose and resolve common issues:
-
Check Physical Connections:
Confirm all cables are properly seated and connected. Make sure link lights on interfaces are present. A missing link light could point to disconnected cables, faulty hardware, or hardware compatibility issues. -
Verify Interface Status:
Use CLI commands likeshow interfaceandshow interface ip briefto check the operational status. Mismatches between the physical status (link light) and GUI/CLI reports often indicate a software or version issue. Restart the affected interface or device if needed[7]. -
Review Configuration:
Ensure each interface is enabled and properly configured with the correct nameif, IP address, speed, and duplex settings. For VLAN and EtherChannel interfaces, confirm correct VLAN IDs and group configuration. -
Test Connectivity:
Utilize commands likepingandtraceroutefrom the device or diagnostic CLI to test reachability. For management interfaces, useping systemtoward your Firepower Management Center (FMC) to validate management network connectivity[5][6]. -
Check Access Policies and NAT Rules:
Access control or incorrect NAT rules can drop legitimate traffic. Review rules in FMC or FDM, and simulate traffic flow withpacket-tracer. Adjust misconfigured rules or NAT settings as needed[9][10]. -
Monitor Resource Utilization:
High CPU or memory usage can impact interface operations. Check withshow cpu usageandshow memory statistics. Investigate and resolve any excessive resource consumption[8]. -
Check Logs and Alerts:
Review event logs in the FMC/FDM and useshow loggingon the CLI to identify dropped traffic, policy violations, or hardware errors. Ensure logging is enabled for relevant interfaces and rules[10]. -
Investigate Software Versions and Known Bugs:
If you encounter unexpected interface behavior, consult the release notes and Cisco bug tracker for known issues with your Firepower OS version. Some versions require hotfixes for interface or HA bugs[7]. -
Use Diagnostic Tools:
Leverage diagnostic CLI,system support diagnostic-cli, and built-in tools likecapturefor live packet captures orpacket-tracerfor virtual packet path analysis[9][10]. -
Restart or Reseat Modules if Needed:
As a last resort, reboot the device or reseat interface modules if physical/operational mismatches persist and no software fixes resolve the issue.
Best Practice: Always document your troubleshooting steps and results. If an issue persists, gather all relevant logs and configuration data before escalating to Cisco TAC for further analysis.
Conclusion
Throughout this blog post, we explored the many essential aspects of Cisco Firepower interfaces and how they play a critical role in the overall functionality and security of your network deployment.
Here are the key takeaways:
- Interface Types: From physical and VLAN subinterfaces to bridge groups and EtherChannels, Firepower offers customizable interface options to suit different deployment scenarios, whether routed or transparent.
- Configuration Steps: Setting up interfaces is a structured process. It starts with enabling them, assigning names and IP addresses, and ensuring all changes are deployed through Firepower Management Center (FMC) or Device Manager.
- CLI Efficiency: The command-line interface (CLI) grants you powerful control for monitoring and managing interfaces. Essential commands like
show interface,configure network, andshow routeare indispensable for everyday operations. - CLI Modes: With multiple access levels (from User EXEC to Expert Mode), understanding where to use each mode ensures that tasks are performed securely and accurately.
- Operational Considerations: Notable notes like the management interface's role, VLAN tag limitations, and hardware-specific capabilities help you avoid configuration pitfalls.
- Troubleshooting Tips: From basic cable checks to advanced packet captures and analyzing logs, we covered a comprehensive step-by-step approach to diagnose and resolve interface issues effectively.
Cisco Firepower interfaces are incredibly flexible and powerful, but managing them well requires a deep understanding of both the interface types and the tools available to you. Whether you're setting up a new deployment, integrating segmented VLANs, or troubleshooting connectivity issues, mastering the interface configuration workflow will help you achieve better network performance and stronger security postures.
Thanks for reading! We hope this guide gave you the confidence and clarity needed to take control of your Firepower interfaces like a pro. Until next time—stay secure and keep configuring! 🔐🔥