Table of Contents
- Overview
- Key Definitions
- Common IPS Technologies
- Core Features of Modern IPS
- Typical IPS Deployment Modes
- Leading IPS Vendors
- IPS Use Cases
- Example IPS Rule
- Troubleshooting & Best Practices
- Conclusion
Overview of Intrusion Prevention Systems (IPS)
What Is an Intrusion Prevention System (IPS)?
An Intrusion Prevention System (IPS) is a proactive network security solution designed to detect, prevent, and respond to potentially harmful network activities. Unlike systems that simply identify threats, an IPS can automatically block or neutralize suspicious traffic in real time. Modern IPS technologies analyze network packets, inspect system activity, and use a combination of detection methods to safeguard against known and emerging threats.
Why You Need to Know About IPS
- Growing Threat Landscape: Cyberattacks are becoming more sophisticated, targeting organizations of all sizes. An IPS acts as a crucial frontline defense against malware, exploits, and unauthorized access.
- Compliance Requirements: Many regulatory frameworks (such as PCI DSS, HIPAA, and ISO/IEC 27001) require organizations to implement intrusion prevention controls to protect sensitive data.
- Business Continuity: Attacks like ransomware, data breaches, or denial-of-service can disrupt operations and cause financial and reputational damage. An IPS helps ensure network availability and reliability.
- Proactive Protection: Prevention is more effective than remediation. IPS solutions actively block threats, minimizing the risk of compromise and reducing incident response costs.
How an IPS Works
An IPS continuously monitors network traffic and system behavior to identify malicious or policy-violating activities. It does this through several key processes:
- Traffic Analysis & Inspection:
- Examines packets as they flow through the network using deep packet inspection.
- Looks for known signatures and patterns of malicious behavior.
- Detection Techniques:
- Signature-Based: Compares activity against databases of known attack signatures.
- Anomaly-Based: Flags traffic that diverges from established baselines of normal behavior.
- Policy-Based: Applies administrator-defined rules to stop unauthorized or suspicious actions.
- Hybrid Approaches: Combines multiple methods for more comprehensive coverage.
- Threat Prevention Actions:
- Blocks or drops malicious network packets.
- Terminates harmful connections.
- Quarantines affected systems or restricts certain user actions.
- Notifies security teams and logs detailed events for analysis.
- Integration:
- Works in tandem with firewalls, SIEMs, and other security platforms.
- Leverages threat intelligence feeds for updates on new threats.
By employing these strategies, an IPS serves as an essential component in an organization’s security architecture, providing automated, real-time defense against a wide spectrum of cyberattacks.
Key Definitions
Here are essential terms to know when working with Intrusion Prevention Systems (IPS):
- Intrusion Prevention System (IPS): A network security technology that monitors network traffic, detects malicious activities, logs events, reports incidents, and can actively block or prevent threats.
- Intrusion Detection System (IDS): Security technology that monitors network or system activities for malicious activity or policy violations and alerts administrators but does not block the activity.
- Signature-Based Detection: Technique that uses known patterns (signatures) of malicious threats to identify and block them.
- Anomaly-Based Detection: Identifies threats by detecting deviations from established normal behavior in network traffic.
- False Positive: When legitimate activity is incorrectly identified as malicious by the IPS.
- False Negative: When actual malicious activity goes undetected by the IPS.
- Deep Packet Inspection: The process of examining the data (payload) within network packets, not just the headers.
- Zero-Day: A new, previously unknown security vulnerability, often exploited before a patch is available.
- Threat Intelligence: Information about existing or emerging threats that helps inform and improve security decisions and responses.
Common IPS Technologies
Intrusion Prevention Systems (IPS) use various technologies to detect and prevent threats in network environments. Here are the key types and their detection approaches:
- Signature-Based Detection: Compares network traffic to a database of known threat patterns (signatures). This method is highly effective against recognized threats but may miss new or unknown attacks.
- Anomaly-Based Detection: Establishes a baseline of normal network behavior and detects deviations. Suspicious activities outside this baseline trigger alerts or preventive actions, making this approach useful against zero-day attacks.
- Policy-Based Detection: Uses administrator-defined security policies to identify unauthorized actions. If traffic violates these rules, the IPS responds according to the policy.
- Hybrid Detection: Combines two or more detection methods (such as signature and anomaly-based) for broader and more accurate threat coverage.
Additionally, IPS can be categorized by deployment:
- Network-Based IPS (NIPS): Monitors and protects entire network segments by analyzing traffic passing through critical points.
- Host-Based IPS (HIPS): Installed on individual devices to monitor inbound and outbound traffic specific to that host.
- Wireless IPS (WIPS): Focuses on detecting threats and unauthorized devices on wireless networks.
- Network Behavior Analysis (NBA): Examines network traffic patterns to spot abnormal behaviors such as large-scale attacks or new malware.
| Category | Description |
|---|---|
| Signature-Based | Detects threats using a database of known attack signatures. Quick and accurate for known threats, but needs regular updates. |
| Anomaly-Based | Identifies deviations from established normal network activity. Useful for detecting new or unknown threats. |
| Policy-Based | Enforces custom security rules to block unauthorized behavior or policy violations. |
| Hybrid | Integrates multiple detection methods for enhanced security and better threat coverage. |
Understanding these common IPS technologies allows organizations to choose the right approach for protecting their networks from evolving cyber threats.
Core Features of Modern IPS
Modern Intrusion Prevention Systems (IPS) deliver comprehensive protection against a wide variety of cyber threats by integrating several advanced features. Below are the core capabilities that define a robust, effective IPS:
- Real-Time Threat Detection and Prevention: Constantly monitors network traffic to identify and block malicious activity as it happens, using advanced pattern matching, behavioral analysis, and machine learning for timely threat response.
- Automated Response and Blocking: Takes immediate action to stop threats—such as dropping malicious packets, blocking suspicious IP addresses, terminating connections, or dynamically updating firewall rules—without human intervention.
- Traffic Analysis and Deep Packet Inspection: Examines network packets for malicious content or anomalies, not only within headers but also in payloads, to thoroughly detect sophisticated attacks.
- Signature and Anomaly-Based Detection: Uses a combination of signature databases (for known attacks) and behavioral/anomaly analysis (for new or unknown threats), creating layered and adaptive defense mechanisms.
- Comprehensive Logging and Alerting: Records all security events, generates actionable alerts, and provides detailed reporting for incident investigation, compliance, and ongoing security improvement.
- Policy and Rule Management: Enables customization of detection rules and security policies to align with organizational needs, fine-tuning response actions and minimizing false positives.
- Integration with Other Security Tools: Seamlessly works with firewalls, SIEMs, and endpoint systems to provide coordinated threat defense and a unified security posture.
- Threat Intelligence Feeds: Leverages updated threat intelligence sources to stay ahead of emerging risks, ensuring ongoing protection against the latest exploits and attack vectors.
These core features empower organizations to proactively guard against advanced attacks by detecting, preventing, and responding to threats in real time—thus forming a cornerstone of any modern cybersecurity strategy.
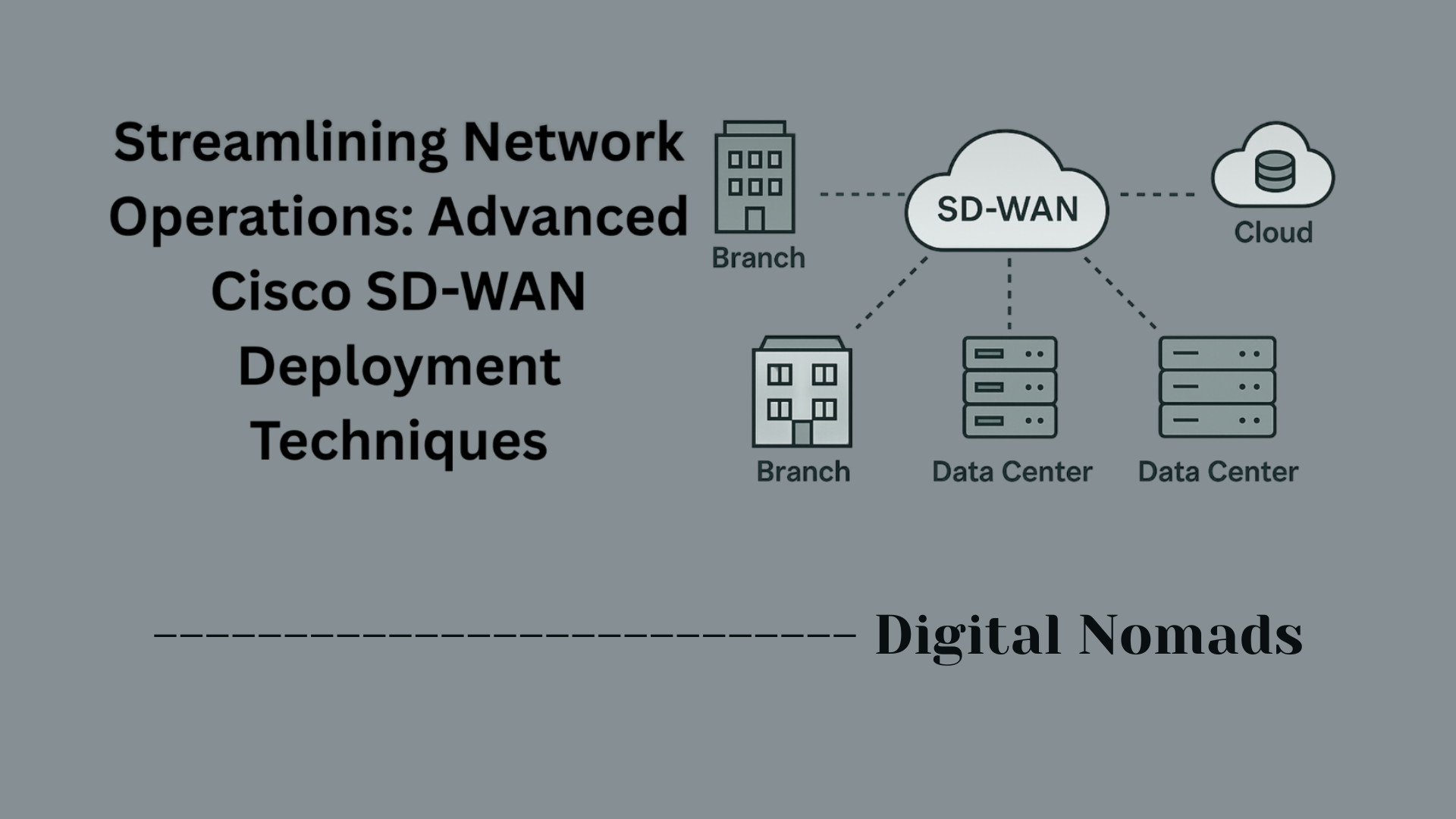
Typical IPS Deployment Modes
Intrusion Prevention Systems (IPS) can be deployed in several modes to fit different security and network requirements. Choosing the right mode ensures an effective balance between security, performance, and operational impact. Below are the most common IPS deployment modes:
-
Inline Mode:
The IPS is placed directly in the traffic path between source and destination devices. All network traffic passes through the IPS, allowing it to inspect and, if necessary, block malicious packets in real time. Inline mode offers the highest level of proactive security because threats are prevented before reaching their targets. However, network performance can be impacted if the IPS device experiences high load or failure.
- Also known as “active” or “in-path” mode. Ideal for environments where blocking threats is a priority. -
Passive Mode:
The IPS monitors network traffic by receiving a copy (mirror) of the network flow via SPAN port, TAP, or other network mirroring technology. It analyzes traffic and generates alerts if suspicious activity is detected, but it does not block or alter the traffic in real time. Passive mode is useful for detection and logging, but it cannot prevent threats from reaching their targets.
- Commonly used for monitoring, forensics, or in environments where network interruption must be minimized. - Inline Tap/Monitor Mode: In this hybrid approach, the IPS device is physically in the line of traffic but configured only to monitor and alert on threats rather than block them. This provides visibility while preparing for potential switch to full inline prevention.
-
Host-Based and Network-Based:
IPS can be tailored for specific deployment scenarios:
- Network-based IPS (NIPS): Protects the entire network by inspecting traffic at strategic points, such as gateways or perimeter devices.
- Host-based IPS (HIPS): Installed on individual endpoints or servers to monitor and block malicious activity specific to that host.
| Deployment Mode | Description | Action Capability | Common Use Cases |
|---|---|---|---|
| Inline | IPS sits in the direct traffic flow, inspecting and blocking malicious packets before they reach their destination. | Detect & Prevent (Block) | Proactive network security, perimeter defense, active mitigation |
| Passive | Receives a mirrored copy of traffic for analysis; does not block threats directly. | Detect Only (Alert) | Network visibility, compliance monitoring, incident response |
| Inline Tap/Monitor | IPS is inline but set to monitoring mode; inspects traffic and generates alerts without blocking. | Detect (Alert) without Blocking | Testing/transitioning from passive to inline prevention |
| Host-Based IPS | Deployed on individual endpoints to monitor and block malicious behavior at the host. | Detect & Prevent (Block) on host | Server protection, endpoint security, tailored defense |
| Network-Based IPS | Deployed at network perimeters or critical segments, monitoring traffic across entire network segments. | Detect & Prevent (Network-wide) | Enterprise or data center security, infrastructure defense |
Understanding these deployment modes helps organizations select and configure their IPS for maximum effectiveness based on their unique network architecture and risk profile.
Leading IPS Vendors
Modern Intrusion Prevention Systems (IPS) are provided by a variety of established cybersecurity vendors, each offering unique strengths for diverse network environments and security requirements. Below are some of the leading IPS vendors in 2025, along with key features that set their solutions apart:
- Cisco Secure IPS: Offers advanced threat detection, broad integration with other security solutions, and robust network visibility. Cisco is renowned for its reliable hardware options and its extensive threat intelligence network[1][8].
- Check Point Quantum IPS: Delivers high-speed, next-generation intrusion prevention with low false positives, integrating with firewalls and providing continuous updates to defend against new attacks[1][8].
- Palo Alto Networks: Integrates IPS features within its next-generation firewall platform, known for customizable policies and strong active blocking capabilities[1].
- Fortinet FortiGuard IPS: Combines signature-based and anomaly detection, frequent security updates, and seamless integration with other Fortinet security tools[1].
- Trend Micro TippingPoint: Specializes in machine learning-driven intrusion detection, effective SSL inspection, and deep packet inspection for large enterprise networks[2][8].
- Trellix Network Security (formerly McAfee): Offers advanced DDoS protection, sandboxing, and comprehensive global threat intelligence integration[2][3].
- Zscaler Cloud IPS: Provides always-on, cloud-delivered IPS with full TLS/SSL inspection, suitable for distributed enterprises seeking scalable, cloud-native solutions[1][8].
- Hillstone S-Series IPS: Delivers integrative cybersecurity for digital assets, with support for edge-to-cloud coverage and detailed network behavioral analysis[2].
| Vendor | Key Features | Best For |
|---|---|---|
| Cisco Secure IPS | Advanced detection, broad integration, network visibility | Enterprises seeking robust, scalable protection |
| Check Point Quantum IPS | Low false positives, high performance, virtual patching | Large organizations and data centers |
| Palo Alto Networks | Customizable policies, integrated with NGFW | Organizations needing granular control |
| Fortinet FortiGuard IPS | Frequent updates, integrated with Fortinet products | Companies using the Fortinet ecosystem |
| Trend Micro TippingPoint | Machine learning, SSL inspection, high throughput | High-traffic enterprise environments |
| Trellix (McAfee) IPS | DDoS protection, sandboxing, global threat intelligence | Enterprises with advanced threat detection needs |
| Zscaler Cloud IPS | Cloud-native, full SSL inspection, easy scaling | Distributed or cloud-focused organizations |
| Hillstone S-Series IPS | Edge-to-cloud coverage, behavior analytics | Enterprises needing broad digital protection |
Selecting a leading IPS vendor should be based on organizational size, network complexity, integration needs, and specific threat management priorities. Ongoing evaluation of new features and compatibility with existing infrastructure is essential for maximizing security effectiveness.
IPS Use Cases
Intrusion Prevention Systems (IPS) are critical in defending networks and systems from cyber threats. Below are common use cases where IPS technology provides essential protection:
- Perimeter Security: IPS is deployed at network edges to detect and block external attacks before they penetrate the internal network. This protects against threats such as hacking attempts, malware, and unauthorized access.
- Data Center Protection: Within data centers, IPS safeguards critical servers and applications against both internal and external cyberattacks, ensuring availability and data integrity.
- Lateral Movement Prevention: IPS monitors internal network segments to prevent attackers from moving laterally between systems, limiting the spread of malware or breaches.
- Cloud Environment Defense: IPS solutions protect cloud infrastructures—public, private, and hybrid—from threats like account takeovers, data breaches, and misconfigurations.
- Regulatory Compliance: Organizations use IPS to meet compliance standards such as PCI DSS and HIPAA, ensuring continuous monitoring and prevention of security policy violations.
- DDoS Attack Mitigation: IPS detects unusual traffic patterns indicative of Distributed Denial of Service (DDoS) attacks and takes action to block or limit malicious traffic to maintain service availability.
- Advanced Threat Detection: IPS employs signature, anomaly, and behavioral analysis to identify and neutralize advanced persistent threats (APTs) and zero-day exploits.
- Automated Phishing Response: Some advanced IPS, leveraging AI, can automatically identify phishing attempts in emails and isolate affected endpoints to minimize damage.
- Industrial Control System Security: IPS protects critical infrastructure components from cyberattacks by monitoring and blocking exploits targeting industrial protocols.
By applying IPS appropriately across these use cases, organizations can enhance their cybersecurity posture, reduce risks, and ensure business continuity.
Example IPS Rule
An IPS rule enables organizations to define specific criteria for identifying and preventing malicious activities on their networks. Below is a sample IPS rule in a style similar to Snort, one of the most popular open-source IPS solutions:
alert tcp any any -> 192.168.0.0/16 80 (msg:"HTTP Connection Attempt"; sid:1000001; rev:1;)
- alert tcp – The action and protocol. Here, “alert” means it will generate an alert, and “tcp” specifies the protocol.
- any any -> 192.168.0.0/16 80 – The source and destination. “any any” matches all source IPs and all source ports. The arrow indicates traffic going to the destination IP range (192.168.0.0/16) and destination port 80 (typically HTTP).
- msg:"HTTP Connection Attempt" – Message describing the rule’s purpose, displayed in alerts.
- sid:1000001 – A unique Snort rule identifier (number).
- rev:1 – The rule’s revision number.
This rule triggers an alert whenever a TCP connection is attempted from any source to any host within the 192.168.0.0/16 network on port 80. Such rules form the basis for automated, policy-driven threat detection and prevention within an IPS.
Troubleshooting & Best Practices
Ensuring the effectiveness and reliability of an Intrusion Prevention System (IPS) requires ongoing maintenance, fine-tuning, and adherence to industry best practices. This section outlines proven troubleshooting steps and best practices for managing IPS solutions:
Troubleshooting Common IPS Issues
-
Frequent False Positives:
- Review and adjust detection rules or signatures that generate excessive false alerts.
- Tune sensitivity levels or update baseline profiles to better match normal network behavior.
- Collaborate with end-users to identify legitimate activities mistakenly flagged by the system.
-
Missed Threats (False Negatives):
- Ensure the IPS is operating with updated threat signatures and anomaly detection profiles.
- Test rule sets with current attack simulations and penetration tests.
- Integrate external threat intelligence feeds to enhance detection accuracy.
-
Performance Impact:
- Monitor CPU, memory, and network utilization on the IPS device regularly.
- Optimize the number and specificity of detection rules to reduce unnecessary load.
- Consider hardware upgrades or distributed deployment for high-throughput environments.
-
Update Failures:
- Check network connectivity to update servers and ensure that IPS devices have appropriate permissions.
- Schedule regular, automatic updates to minimize manual intervention and lapses in protection.
Best Practices for IPS Management
- Regularly Update Signatures and Software: Maintain up-to-date detection capabilities by applying vendor-released signatures and firmware updates.
- Fine-Tune Detection Rules: Customize policies and rules according to the organization’s threat landscape and network profile, reducing unnecessary alerts and missed threats.
- Monitor and Analyze Logs: Set up log reviews or SIEM integration for timely detection of trends, repeated attacks, or system anomalies.
- Baseline and Audit Normal Traffic: Regularly profile network activity to distinguish between normal and suspicious behavior, assisting effective anomaly-based detection.
- Implement Layered Security: Integrate IPS with firewalls, endpoint protection, and other security systems for comprehensive defense-in-depth.
- Conduct Periodic Testing: Run penetration tests, vulnerability assessments, and red team exercises to validate IPS efficacy and response capabilities.
- Document and Review Policies: Establish clear IPS management policies, update them as threats evolve, and train security personnel on best practices and incident response.
By following these troubleshooting steps and best practices, organizations can maximize their IPS investment—minimizing disruptions while ensuring robust, continuous protection against emerging cyber threats.
Conclusion
Throughout this blog post, we've taken a deep dive into the world of Intrusion Prevention Systems (IPS)—a cornerstone of modern cybersecurity. You’ve learned what an IPS is, how it works, and why it's crucial in today’s ever-evolving threat landscape.
Key Takeaways:
- What IPS Is: An Intrusion Prevention System is a powerful security tool that actively monitors, detects, and prevents malicious activity on your network. It doesn't just alert; it takes action to stop threats in their tracks.
- Why It Matters: With cyber threats becoming more sophisticated, relying solely on traditional firewalls or passive detection systems isn't enough. An IPS adds a proactive layer of protection that helps maintain business continuity and regulatory compliance.
- Core Technologies: We covered the different methods of threat detection—signature-based, anomaly-based, policy-based, and hybrid—along with the typical forms IPS can take, from Host-based to Network-based solutions.
- Deployment Flexibility: Whether using inline (active) or passive modes, IPS systems can be tailored to fit your network infrastructure and risk tolerance.
- Real-World Applications: From shielding data centers to protecting cloud environments and preventing DDoS attacks, IPS solutions are versatile and essential in both enterprise and mid-sized business environments.
- Vendors & Tools: We explored leading IPS vendors including Cisco, Palo Alto Networks, Fortinet, and others, giving you real options to evaluate based on your needs.
- Implementation Tips: With hands-on examples, rules, troubleshooting strategies, and best practices, you're armed with the knowledge to deploy, manage, and maintain a high-performing IPS.
As we continue moving deeper into a connected world, implementing proactive, intelligent cybersecurity solutions like IPS becomes more critical than ever. Whether you’re a security professional, a network engineer, or someone just beginning your cybersecurity journey, understanding IPS gives you a stronger footing in defending digital environments.
Thanks for reading! We hope this blog post helped demystify the world of Intrusion Prevention Systems. Stay safe, stay secure—and don’t forget to check back soon for more cybersecurity insights and best practices! 🚀🔒