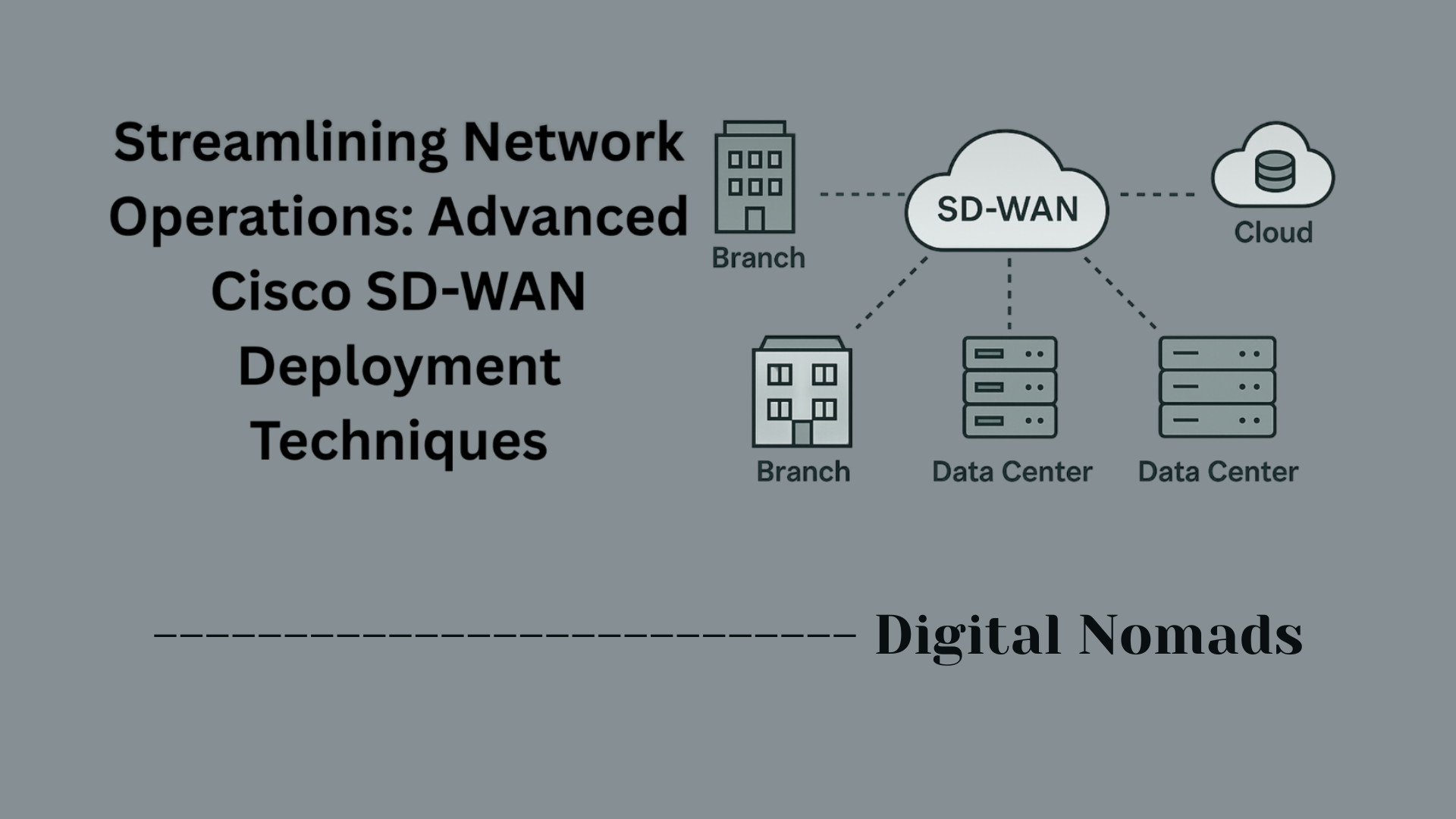
Table of Contents
- Overview
- Key Terms and Definitions
- Licensing and Prerequisites
- How Cisco Firepower URL Filtering Works
- Configuration Overview (Summary)
- Best Practices
- Limitations and Notes
- Conclusion
Cisco Firepower: URL Filtering Overview
What Is Cisco Firepower URL Filtering?
Cisco Firepower URL Filtering is a security solution embedded in Cisco’s next-generation firewalls. It allows organizations to control and monitor which websites users can access based on URL categories and threat reputations. The feature leverages a dynamic, cloud-based database to classify billions of web addresses and continuously evaluates web requests in real time.
Why Do You Need Cisco Firepower URL Filtering?
- Enhance Security: Blocks user access to malicious, compromised, or phishing sites, reducing the risk of malware infections and data breaches.
- Boost Productivity: Prevents visits to non-work-related or distracting websites, helping organizations maintain focus and productivity.
- Compliance & Policy Enforcement: Ensures internet usage stays within regulatory boundaries and company policies by restricting access to certain categories.
- Reduce Risk Exposure: Leverages Cisco’s up-to-date threat intelligence, guarding against newly discovered harmful sites and risky web content.
- Customize Access: Allows administrators to create granular, business-specific filtering rules, balancing security with operational needs.
How Does Cisco Firepower URL Filtering Work?
- URL Classification and Reputation Lookup:
Every web request from the network is checked against Cisco’s huge, constantly updated cloud database. URLs are classified by content category (such as Social Media, News, Adult Content) and assigned a reputation score (like Trusted, Neutral, or High Risk). - Policy-Based Enforcement:
Administrators define policies in the Firepower Management Center to allow or block access based on these categories and reputations. Policies can also include explicit manually managed allow-lists and block-lists for special cases. - Cloud and Local Intelligence Blend:
Firepower devices keep a local cache of frequently used URL data to speed up processing. If a URL is not found locally, the device quickly queries Cisco’s cloud for the latest classification and reputation information. - HTTP and HTTPS Handling:
- For unencrypted (HTTP) traffic, the firewall can inspect the full URL path for detailed filtering.
- For encrypted (HTTPS) traffic, filtering is done at the domain level unless SSL decryption is enabled, in which case the full URL can be evaluated.
- Automation and Updates:
The database of categories and reputations is automatically updated at regular intervals, ensuring that filtering decisions always use the most current intelligence. - Logging and Reporting:
Every allow/block decision is logged, enabling detailed reporting for compliance, audit trails, and fine-tuning of filtering policies.
In summary, Cisco Firepower URL Filtering empowers organizations to protect users from evolving web threats, enforce acceptable use, and adapt filtering for specific business needs—all through a blend of real-time threat intelligence and flexible policy management.
Key Terms and Definitions
These are the foundational terms you’ll encounter when working with Cisco Firepower URL Filtering:
- URL Filtering: The process of allowing or blocking access to websites based on their web address (URL), using defined policies to help protect the network and enforce organizational standards[2][3].
- Category (URL Category): A general classification applied to websites, such as Social Networking, News, Gambling, or Job Search. Every URL may belong to one or multiple categories, used to drive filtering decisions[2][6].
- Reputation: A risk score assigned to a URL based on Cisco’s global threat intelligence. Scores range from High Risk or Untrusted to Well Known or Trusted, reflecting how likely the site is to be malicious or inappropriate[2][6].
- Manual URL Filtering: The creation of custom lists, objects, or groups of URLs that admins specifically allow or block, regardless of their category or reputation rating[2][3].
- Cisco Collective Security Intelligence (CSI): Cisco’s continually updated cloud-based service that provides URL categories and reputation scores for filtering decisions in real time[2].
- Access Control Policy: The set of rules in Firepower Management Center (FMC) that defines how URLs are filtered, including allowed categories, reputations, and exceptions[3].
- SSL Decryption: A process that enables deeper inspection of encrypted (HTTPS) traffic by decrypting it, allowing Firepower to filter not just by domain, but by the full URL path[5].
- Security Intelligence: A related feature allowing Firepower to block known malicious URLs, domains, and IPs, operating alongside— but separate from—basic URL Filtering[2][3].
- URL Objects/Groups: Administrative tools in FMC used to create, group, and manage custom URL lists for policy exceptions[5].
Licensing and Prerequisites
Before you can fully utilize Cisco Firepower URL Filtering, make sure these licensing and system requirements are addressed:
- URL Filtering License: A valid URL Filtering subscription license is required to use category and reputation-based filtering. This license must be assigned and active on each managed device where you intend to deploy advanced filtering. Without it, only manual URL filtering (blocking or permitting individual URLs or groups) is available, not category or reputation filtering[1][4][5][7].
- Device Compatibility: Check that your Firepower device and software version support URL Filtering. Some entry-level devices may have limitations or require sufficient memory to store data sets for URL categories and reputations[12].
- Internet Access: The Firepower Management Center (FMC) must be able to communicate with Cisco’s cloud (Cisco Collective Security Intelligence) to download and update the URL category and reputation data sets. Outbound internet connectivity is required for initial setup and ongoing updates[5][9][12].
- Licensing Prerequisites: For some older devices or classic platforms, other core licenses (like Protection or Control) must be enabled before you can activate URL Filtering[10][13].
- Assigning the License: Apply and enable the URL Filtering license in the FMC. The feature will not operate until the license is assigned at both the management and device level[5][6][12].
- Best Practice: Enable automatic updates for the URL Filtering threat data—this ensures that new threats, categories, and changes to domain reputation are always reflected in your policies without manual intervention[12].
Summary Table
| Requirement | Description |
|---|---|
| URL Filtering License | Needed for category and reputation filtering. Manual filtering by explicit URLs possible without it. |
| Device & Software Support | Ensure your Firepower device and software version support the feature. |
| Internet Access (FMC) | Required for URL data downloads and updates from Cisco’s cloud. |
| Other Core Licenses | Some older platforms require Protection/Control licenses first. |
| License Assignment | License must be assigned on both FMC and each managed device for filtering to function. |
| Automatic Updates | Recommended to keep the system’s threat data up to date. |
How Cisco Firepower URL Filtering Works
The Cisco Firepower URL Filtering feature operates using a mix of cloud intelligence, real-time categorization, and granular policy controls. Here’s a step-by-step breakdown of how it functions in practice:
- Enable URL Filtering & Download Data: When enabled, the Firepower Management Center (FMC) queries Cisco’s cloud to download the latest URL category and reputation dataset. This is pushed to all managed devices for local storage and quick lookups[1][4].
- Intercept and Inspect Traffic: The Firepower device monitors outgoing web requests (HTTP/HTTPS) from your network. For each request, it checks the URL’s category and reputation using its locally stored data. If the classification isn’t available locally, it will query the Cisco cloud in real time[1][2].
-
Filter by Category and Reputation:
Each URL is evaluated based on:
- Category: Examples include Social Networking, News, Gambling, and Security Threats. Sites can belong to one or more categories.
- Reputation: Ranges from Trusted (low risk) to Untrusted or High Risk (potential security threats). Reputation is determined by Cisco’s threat intelligence cloud[1][3].
- Manual Exceptions: Admins can define exceptions by whitelisting or blacklisting specific URLs, groups, or lists. Manual rules override broader category or reputation rules and should be placed higher in the rule set[1][5].
-
Handling HTTP and HTTPS:
- HTTP: The system can inspect the full unencrypted URL path and apply policies directly.
- HTTPS: Without SSL decryption, Firepower uses certificate data or the domain from the TLS handshake for filtering, limiting granularity to the domain level. With SSL decryption enabled, deeper inspection is possible, similar to HTTP[3][4][5].
- Automatic Updates & Policy Enforcement: The FMC is set to automatically update its URL dataset at scheduled intervals, ensuring new sites or changes in reputation are rapidly reflected in policy enforcement[4].
- Logging and Reporting: All filtered requests (blocked or allowed) are logged for visibility and analysis. Admins can review these events and refine URL filtering policies over time[1][5].
Summary Table
| Step | Description |
|---|---|
| Enable & Download | FMC queries and receives category/reputation data from Cisco’s cloud. |
| Inspect Traffic | Firepower monitors HTTP/HTTPS requests and checks URL details. |
| Apply Filtering | Policies allow or block URLs by category and/or reputation. |
| Manual Exceptions | Custom allow/block rules can override general filtering policies. |
| Handle HTTP/HTTPS | HTTP gets full inspection; HTTPS filtering is domain-based without decryption and full-path with SSL decryption. |
| Automatic Updates | FMC updates URL data regularly to respond to new threats and sites. |
| Logging/Reporting | All actions are logged and available for admin review and tuning. |
Configuration Overview (Summary)
This section summarizes the essential steps to set up and deploy Cisco Firepower URL Filtering in your environment:
- Obtain & Assign License: Purchase a valid URL Filtering license, then assign it to your Firepower Management Center (FMC) and all managed devices. This unlocks category- and reputation-based filtering capabilities[3][5][7].
- Ensure Device Internet Access: Make sure your FMC can connect to Cisco’s cloud (Collective Security Intelligence) to download and update URL categories and reputations[3][6][7].
- Enable URL Filtering: In the FMC, go to System > Integration and activate the URL Filtering feature. Configure automatic or scheduled updates so your database remains current[3][5].
- Create Filtering Rules: Define access control rules to allow or block traffic by URL category, reputation, or explicit URLs using objects or groups. Prioritize manual exception rules above broader rules when needed[5][6].
- Deploy Policy Changes: After building and saving your rules, deploy the configuration to the managed devices. This pushes all policies live to your network[5][6].
- Monitor & Tune: Check the events and logs in FMC to verify filtering is effective. Adjust rules and categories based on real-world traffic patterns and organizational needs[5][6].
Quick Reference Table
| Step | Description |
|---|---|
| License | Purchase and assign a URL Filtering license for all managed devices. |
| Cloud Updates | Allow FMC to connect to Cisco’s cloud for category/reputation data updates. |
| Enable Feature | Turn on URL Filtering under System > Integration in FMC and schedule updates. |
| Rule Creation | Build rules using categories, reputations, or custom URL objects/groups. |
| Deploy Changes | Apply and push policy to all Firepower devices. |
| Monitor & Tune | Track logs/events and adjust as needed for optimal protection. |
Best Practices
To maximize security and efficiency with Cisco Firepower URL Filtering, follow these best practices during configuration and daily use:
- Combine Category & Reputation Filtering: Always filter based on both web category and reputation scores. This layered approach provides stronger protection, allowing your policy to block not just known malicious sites but also new threats that may not yet be categorized[3][4][5].
- Block All Threat Categories Explicitly: In addition to reputation-based blocking, create rules that block all Cisco-defined Threat categories—such as Malware Sites, Phishing, Spyware & Adware—to further reduce exposure to malicious content[3][5].
- Keep URL Filters Updated: Enable automatic updates of the URL filtering dataset so new websites, domains, and threat reputations are promptly reflected in your policies. Manual or scheduled updates are recommended only if required for compliance[4][5].
- Order Rules Wisely: Place exception or manual filtering rules (like custom allow/block URL lists) higher in the access control policy than broader category or reputation rules. This ensures exceptions take priority and avoids unintended blocking[3][5].
- Handle HTTPS with Care: For effective HTTPS filtering, consider enabling SSL decryption. Without decryption, filtering on HTTPS is limited to the domain level, and subdomain or path-specific rules don’t apply[3].
- Leverage Security Intelligence: Use Cisco’s Security Intelligence feeds alongside URL Filtering to automatically block sites and IP addresses with a known history of malicious activity for defense in depth[4].
- Monitor Logs & Tune Policies: Regularly review URL filtering logs and events in Firepower Management Center. Adjust rules to fix false positives, refine categories, and respond to emerging threats[5].
- Understand Limitations: URL filtering does not inspect URL query parameters (only domains and paths). Memory-limited devices may not cache all data locally and may rely more on cloud lookups, which could affect performance[3].
- Test Before Full Rollout: Validate URL filtering policies in test environments before broad deployment to ensure they don’t impede business operations or cause unexpected site blocks[3][7].
Quick Reference Table
| Best Practice | Why It Matters |
|---|---|
| Combine Category & Reputation | Provides multiple layers of filtering and blocks emerging threats[3][4][5]. |
| Block All Threat Categories | Ensures coverage against known malware, phishing, and spyware[3][5]. |
| Enable Automatic Updates | Keeps threat intelligence timely and policies always effective[4][5]. |
| Prioritize Rule Order | Prevents exceptions from being overruled by general policies[3][5]. |
| Use SSL Decryption | Allows deeper HTTPS filtering for enhanced security[3]. |
| Leverage Security Intelligence | Adds an extra defense layer via real-time blocklists[4]. |
| Audit & Refine Regularly | Adapts to changing network use and threat environment[5]. |
| Know Platform Limits | Prevents performance bottlenecks and missed blocks[3]. |
| Test Policy in Lab | Minimizes disruption and ensures business continuity[3][7]. |
Limitations and Notes
Be aware of these important limitations and technical notes when deploying Cisco Firepower URL Filtering:
- HTTPS Filtering Limitations: For encrypted (HTTPS) traffic, URL filtering without SSL decryption can only evaluate the domain name found in the certificate or TLS handshake—not the full URL path or subdomains. Path-based and subdomain-specific filtering for HTTPS requires an SSL decryption policy[5][6].
-
No Query Parameter Inspection:
Cisco Firepower URL Filtering does not inspect URL query parameters (the part of a URL after
?). Filtering decisions are made solely on the root domain and path[5]. - Manual URL Entry Limits: When adding URLs directly in a single rule via the graphical interface, there may be a per-rule item limit (commonly around 50 entries). To manage larger lists, use URL objects or groups, which scale much higher, or import via APIs[3].
- No Response Pages for HTTPS Blocks: If an HTTPS site is blocked, users do not see a custom HTTP response page because the connection is encrypted. The browser will typically show its own error message instead[5][16].
- Wildcard and Subdomain Support: Wildcard matching and detailed subdomain filtering are limited. For HTTPS, matching is usually only against the main domain, not any subdomains or wildcards[4][6].
- Device Memory Impacts: Firepower devices with lower memory may not cache the complete URL category/reputation database locally, resulting in more frequent lookups to the Cisco cloud—this can slightly delay policy enforcement for uncategorized sites[5].
- High Availability Considerations: Additional considerations and limitations apply for URL filtering with Firepower devices in high availability or failover deployments, such as how cache and policy synchronization is handled[5].
- Encrypted Protocol Awareness: Filtering treats HTTP and HTTPS the same unless access control rules specify otherwise. Extra care is required if you need policy distinctions between protocols[6][7].
- Manual vs. Category Filtering: Manual URL entries and exceptions should appear as higher-priority rules in the policy compared to broad category or reputation rules to ensure intended exceptions are processed[5].
Summary Table
| Limitation | Description |
|---|---|
| HTTPS Domain-Only Filtering | Only the domain is evaluated for HTTPS URLs without SSL decryption[5][6]. |
| No Query Parameter Matching | Query strings are ignored in URL matching and filtering[5]. |
| Manual Rule Entry Limit | GUI has a limit (e.g., 50) for direct URL entries. Use objects/groups for more[3]. |
| No Block Page for HTTPS | Blocked HTTPS sites show browser error, not a custom message[5][16]. |
| Wildcard/Subdomain Limits | Limited support; HTTPS filter matches main domain only[4][6]. |
| Memory/Cloud Lookup | Low-memory devices may rely on frequent cloud checks[5]. |
| High Availability Sync | Cache and sync rules vary in clustered or HA designs[5]. |
| Protocol Matching | HTTP/HTTPS treated the same unless specified in rule[6][7]. |
| Manual Rule Priority | Place manual URLs above broad categories in policies[5]. |
Conclusion
Throughout this blog post on Cisco Firepower URL Filtering, we’ve covered the key elements and operational guidance needed to fully understand and deploy this vital security feature within your network infrastructure. Here’s a quick recap of what we’ve learned:
🔑 Key Takeaways:
- What It Is: Cisco Firepower URL Filtering empowers organizations to control website access using category- and reputation-based intelligence, helping to reduce threat exposure and maintain compliance.
- Why It Matters: URL Filtering enhances security posture, boosts employee productivity, and allows granular traffic management tailored to your organizational needs.
- How It Works: The system inspects outbound traffic, evaluates URLs using real-time Cisco threat intelligence, and applies allow/block rules based on policy. It supports both manual and automated filtering.
- Licensing & Setup: A valid URL Filtering license is necessary. FMC must have internet access to retrieve and refresh Cisco’s cloud-based categorization and reputation databases.
- Configuration Steps: From enabling the feature and setting rule priorities to deploying policies and monitoring logs, Firepower provides a structured approach to traffic control.
- Best Practices: Combine category and reputation filtering, use SSL decryption for HTTPS visibility, organize rule order wisely, and schedule automatic threat intelligence updates.
- Limitations: Be aware of technical constraints such as domain-only filtering for HTTPS (without decryption), limited wildcard and subdomain support, and the lack of response pages for encrypted blocks.
Cisco Firepower URL Filtering is a powerful line of defense in today’s threat landscape. By understanding its core components and configuring it using best practices, you help secure your users, your data, and your organization from unsafe web content and evolving internet threats.
Thanks for following along! If you're implementing or fine-tuning your Firepower URL Filtering setup and have any questions, feel free to drop a comment or reach out for further insights. Happy filtering and stay secure! 🔐🌐