Table of Contents
- Overview
- Core Components
- Appliance Models & Technical Specifications
- Network and Security Services
- Licensing & Management
- Compliance & Integration
- Deployment Guidance
- Conclusion
Overview of Cisco Meraki Security Appliances
What Are Cisco Meraki Security Appliances?
Cisco Meraki security appliances are advanced network security devices that are managed entirely through the cloud. These appliances protect networks by offering a suite of integrated security and networking features—such as firewalls, VPN, threat protection, and traffic management—delivered in a streamlined, easy-to-manage package. Meraki, a subsidiary of Cisco Systems, pioneered the cloud-managed approach, making it possible to deploy, configure, and monitor security devices from any location using an intuitive web-based dashboard.
Why You Need to Know About It
- Simple, Centralized Management: The Meraki Dashboard allows you to oversee all appliances and networks remotely, reducing the need for on-site IT support and making management accessible for organizations of any size.
- Robust Integrated Security: These appliances come with features like stateful firewalls, intrusion detection and prevention (IDS/IPS), advanced malware protection, and content filtering built-in—addressing a wide range of security needs without additional products or complex integrations.
- Scalability and Flexibility: Designed to scale from small offices to large enterprises and even virtual/cloud environments, Meraki’s solution fits diverse deployment scenarios.
- Zero-Touch Provisioning: Devices auto-configure upon connection to the internet, allowing rapid deployment across multiple sites without the need for specialized staff on-site.
- Continuous Updates: Cloud management ensures that appliances always receive the latest security patches and feature enhancements, reducing the risk posed by outdated software.
How It Works
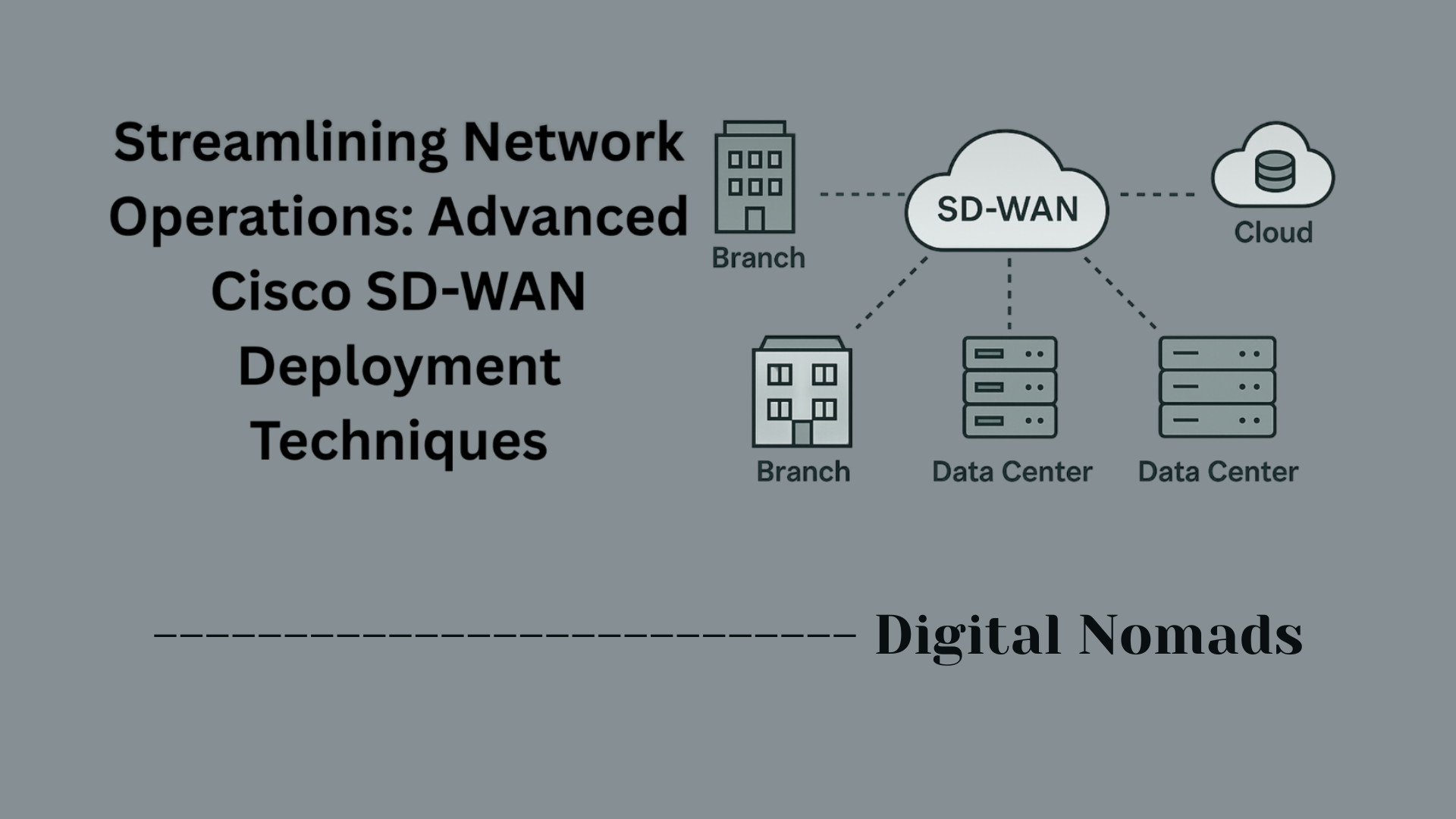
- Cloud Connectivity: Each Meraki appliance securely connects to Cisco’s cloud infrastructure. All configuration, monitoring, and reporting are performed through the Meraki Dashboard, accessible from any browser.
- Unified Policy Enforcement: Network policies and security rules are managed centrally and pushed out to all appliances, ensuring consistent protection and configuration across every location.
- Real-Time Monitoring: The dashboard provides real-time visibility into network traffic, security events, and appliance health. Alerts and analytics are available for quick response and troubleshooting.
- Integrated Security Services: Features like VPN, malware scanning, SD-WAN, and application control operate seamlessly together, managed from a single interface.
- API and Automation: Open APIs allow organizations to integrate Meraki appliances with other IT systems, automate workflows, and fetch analytics or reporting data programmatically.
In summary, Cisco Meraki security appliances bring enterprise-grade security and networking into a highly manageable, cloud-driven package, making them a practical and forward-looking choice for organizations seeking robust protection and operational simplicity.
Core Components
These are the essential building blocks that make Cisco Meraki security appliances deliver robust, cloud-managed network protection:
- Cloud-Based Dashboard: The Meraki Dashboard is an intuitive, web-based management console that allows administrators to configure, monitor, and troubleshoot all Meraki security appliances from anywhere with an internet connection. It provides real-time analytics, role-based access, and centralized updates, simplifying network visibility and maintenance.
- Advanced Stateful Firewall: Meraki security appliances feature a stateful firewall that tracks the state of all active connections and applies rules to both incoming and outgoing traffic. This helps ensure only legitimate, authorized traffic is allowed, providing key perimeter defense.
- Auto VPN & Client VPN: Built-in site-to-site VPN (Auto VPN) enables seamless, encrypted connectivity between multiple locations. Client VPN allows remote users secure access to the network, enhancing flexibility for distributed teams.
- Intrusion Detection & Prevention (IDS/IPS): Integrated IDS/IPS leverages the SNORT engine to monitor network traffic for malicious activity or policy violations, blocking threats before they impact critical systems.
- Content Filtering & Malware Protection: Web content filtering using dynamic databases blocks access to inappropriate or dangerous sites. Advanced Malware Protection (AMP) scans traffic in real-time, defending against viruses and malware.
- Layer 7 Application Visibility & Traffic Shaping: Deep packet inspection allows the appliance to identify applications and users on the network. Administrators can prioritize essential applications or restrict bandwidth-hogging traffic to maintain optimal network performance.
- Integrated SD-WAN Capabilities: Meraki appliances optimize WAN performance with dynamic path selection, failover, and real-time health monitoring, ensuring resilient connectivity across all sites.
- Zero-Touch Deployment: Devices can be pre-configured and automatically provision settings from the cloud at first boot, speeding up rollout and simplifying remote deployments.
Appliance Models & Technical Specifications
Cisco Meraki security appliances come in a range of models suitable for small branches, medium sites, large campuses, data centers, and even virtual/cloud environments. Below you’ll find an overview of key physical models along with their typical technical specifications.
| Model | Use Case | Max Users | Firewall Throughput | VPN Throughput | WAN / LAN Ports | Additional Features |
|---|---|---|---|---|---|---|
| MX67 | Small branch | Up to 50 | 700 Mbps | 300 Mbps | WAN: 2 LAN: 4 |
Optional Wi-Fi / LTE |
| MX68W | Small branch (Wi-Fi) | Up to 50 | 450 Mbps | 200 Mbps | WAN: 2 LAN: 10 (2 PoE+) |
802.11ac Wave 2 Wi-Fi & PoE+ |
| MX85 | Small/Medium branch | Up to 250 | 1 Gbps | 500 Mbps | WAN: 2 SFP, 2 RJ45 LAN: 8 RJ45, 2 SFP |
Rack-mountable |
| MX250 | Large campus / DC | Up to 2,000 | 4 Gbps | 2 Gbps | WAN: 8 SFP LAN: 8 SFP+ |
Dual Power Supplies |
| MX450 | Campus / DC / High capacity | Up to 10,000 | 6 Gbps | 3 Gbps | WAN: 8 SFP LAN: 8 SFP+ |
High availability |
| vMX | Cloud/Virtual environments | Depends on instance size | Up to 1 Gbps | Up to 1 Gbps | Virtual Only | AWS/Azure/GCP |
All appliances run the same Meraki cloud-managed firmware and offer:
- Centralized cloud-based management and real-time monitoring
- Zero-touch provisioning for quick deployments
- Integrated SD-WAN, firewall, VPN, IDS/IPS, and threat protection
- Options for built-in wireless, LTE failover, and PoE/PoE+ ports
- Models for both on-premises and virtual/cloud environments
Network and Security Services
Cisco Meraki security appliances provide an integrated suite of network and security services to protect, control, and optimize your organization’s connectivity. These cloud-managed solutions are designed to deliver robust protection while simplifying IT operations.
- Stateful Firewalling: Controls incoming and outgoing traffic with rules based on stateful packet inspection, application-awareness, and device identification. This helps to ensure only legitimate communications are allowed and threats are blocked at the perimeter.
- Intrusion Detection & Prevention (IDS/IPS): Monitors network traffic for suspicious activity and automates threat blocking using the industry-trusted SNORT engine to protect against known exploits and vulnerabilities.
- Advanced Malware Protection (AMP): Deeply inspects files and network flows for malware, viruses, and ransomware. AMP continuously updates signatures and uses threat intelligence to catch emerging threats.
- Web Content Filtering: Restricts user access to inappropriate, malicious, or non-business-related websites by leveraging constantly updated URL databases.
- SD-WAN & Traffic Shaping: Optimizes application performance and ensures business continuity with dynamic path selection, automatic failover, load balancing, and granular traffic shaping policies.
- Site-to-Site & Client VPN: Secures remote and branch connectivity through encrypted VPNs—both automatic mesh (Auto VPN) between sites and remote-access VPNs for offsite users.
- Secure Guest & BYOD Access: Provides customizable captive portals, VLAN segregation, and access policies to securely onboard guests and personal devices without exposing the core network.
- Threat Intelligence Integration: Leverages real-time security intelligence feeds (powered by Cisco Talos) for rapid detection of global threats and streamlined update delivery.
- Cloud-Based Centralized Management: All services are easily configured, monitored, and managed from the Meraki Dashboard, offering real-time analytics, alerts, and centralized policy enforcement across sites.
- Automated Security Updates: Devices automatically receive the latest firmware and threat definitions from the cloud, ensuring ongoing protection with minimal administrative overhead.
Together, these network and security services make Cisco Meraki security appliances a comprehensive foundation for safeguarding modern, distributed environments with ease and scalability.
Licensing & Management
Cisco Meraki security appliances require an active license to function, access cloud-based management, and receive updates and support. The licensing model is designed to simplify operations and ensure seamless, centralized management for all devices.
How Meraki Licensing Works
- Per Device Subscription: Each Meraki device (security appliance, switch, access point) requires its own license, which can be purchased for a specific term—typically 1, 3, 5, 7, or 10 years.
- Cloud-Based Management Access: Active licensing provides access to the Meraki Dashboard, the centralized web platform for configuring, monitoring, and troubleshooting all devices across one or multiple sites.
- All-Inclusive Support: Licenses include 24/7 technical support, access to new features, ongoing firmware and security updates, and warranty coverage for the licensed duration.
- Automatic Co-Termination: License expiration dates across your network are synchronized automatically for easy renewals, ensuring all devices remain covered and operational.
- Simple Renewals & Upgrades: Expanding the network or renewing coverage is straightforward—simply add or renew licenses for added devices, with all dates auto-adjusting in the dashboard.
| License Component | What’s Included |
|---|---|
| Cloud Management | Centralized dashboard access, network-wide control, and real-time analytics |
| Support & Warranty | 24/7 technical support, advanced hardware replacement, and warranty coverage |
| Firmware & Threat Updates | Continuous feature improvements and security patches pushed automatically |
| API & Automation | Full access to Meraki APIs and automation tools for network management tasks |
Management Features
- Single-Pane Dashboard: Manage all appliances, users, and policies from a single web portal—no on-site controllers required.
- Role-Based Administration: Assign granular access levels to team members for streamlined collaboration and compliance.
- Zero-Touch Provisioning: New devices are configured and updated automatically by connecting to the cloud, minimizing deployment time.
- Automated Monitoring & Alerts: Receive real-time alerts on network health, device status, and license expiration to ensure uptime and security.
- Comprehensive Reporting: Generate historical analytics and audit logs for user activity, configuration changes, and network performance.
With its licensing and management approach, Cisco Meraki empowers organizations to easily scale, secure, and maintain their network with predictable costs and minimal administrative overhead.
Compliance & Integration
Cisco Meraki security appliances are designed to meet diverse compliance needs and provide seamless integration with third-party solutions, helping organizations maintain network integrity, satisfy regulatory demands, and unify IT operations.
Compliance Standards
- PCI DSS: Meraki appliances meet Payment Card Industry Data Security Standard (PCI DSS) requirements, supporting secure cardholder data environments for retail, hospitality, and other industries that require strict payment processing security.
- SOC 2, ISO, and More: Meraki data centers and cloud services are audited for SOC 2 Type II, ISO 27001, and other international standards, ensuring robust data protection, privacy, and operational reliability.
- GDPR & HIPAA: Features and policies support General Data Protection Regulation (GDPR) and Health Insurance Portability and Accountability Act (HIPAA) compliance, helping organizations safeguard sensitive data in healthcare and other regulated fields.
- FedRAMP: Select Meraki solutions are built for the high standards of U.S. federal government cloud compliance, simplifying adoption and management in the public sector.
- Regular Security Audits: Appliances and cloud environments undergo routine vulnerability assessments, penetration testing, and audits to ensure continued protection and compliance.
- Configurable Security Controls: Administrators can enforce strong encryption (e.g., WPA2/WPA3), segment networks, restrict access, and implement policies aligned with strict compliance frameworks.
Integration Capabilities
- API Access: The Meraki Dashboard offers a powerful API for automating management, data collection, and configuration across devices and third-party systems.
- SIEM & Log Integration: Appliances can send syslog and event data to Security Information and Event Management (SIEM) tools and log collectors, supporting centralized monitoring and rapid response.
- Identity & Access Management (IAM): Integrates with directory services and Single Sign-On (SSO) providers for secure user authentication, role-based access, and streamlined onboarding.
- Cloud Security & XDR: Compatible with Cisco XDR and Secure Cloud Analytics for unified threat detection, incident response, and network telemetry enrichment.
- Third-Party Applications: Integrates with ITSM, asset management, guest access (captive portal), and documentation platforms to enhance workflows and user experiences.
- Native Cisco Ecosystem Integration: Works seamlessly with other Cisco cloud and security offerings—including Secure Connect, Umbrella, Duo, and Cisco Spaces—for a comprehensive, future-ready architecture.
By aligning with strict compliance standards and providing rich integration capabilities, Cisco Meraki security appliances enable organizations to protect sensitive information, simplify audits, and unify management across complex environments.
Deployment Guidance
Cisco Meraki security appliances are designed for simple, reliable, and scalable deployment across organizations of all sizes. Follow this step-by-step approach to ensure a smooth setup and optimal configuration:
- Prepare the Environment: Identify the installation site, confirm network topology (WAN, LAN, VPN needs), and gather necessary details such as ISP information and VLAN/subnet plans. Allocate rack space or desktop location and ensure reliable power and network cabling.
- Claim and Add Appliance: Log in to the Meraki Dashboard. Claim your device using its serial number or order number. Create a network (or add to an existing one) and assign the appliance for centralized cloud management.
- Register and Basic Internet Access: Connect the WAN port of the appliance to your ISP handoff or main uplink. The device will automatically establish a secure link to the Meraki cloud for provisioning once it detects an active internet connection.
- Configure Network Settings: Set up WAN IP assignment (dynamic via DHCP or static as provided by ISP). Configure DNS, LAN addressing, and VLANs. Define roles for each port (WAN, LAN, or multi-purpose).
- Establish LAN & VLAN Structure: Plan for multiple VLANs to segment guest, employee, and critical device traffic. Assign appropriate subnet ranges and interface IPs for each VLAN. Enable DHCP or configure static addressing as required for each subnet.
- Security, Firewall, and Threat Protection: Customize firewall rules (Layer 3 & Layer 7) to control both inbound and outbound traffic. Enable Intrusion Detection/Prevention (IDS/IPS), Advanced Malware Protection (AMP), and web filtering for robust security.
- Enable VPN Services: Configure site-to-site Auto VPN for branch interconnectivity and client VPN for secure remote access. Define authentication methods and access policies according to organizational requirements.
- Integrate with the Network: Connect downstream switches, access points, and other devices. Verify VLAN/tagging consistency and test connectivity for both wired and wireless segments.
- Optimize and Monitor: Implement traffic shaping and SD-WAN policies as needed. Monitor appliance status, traffic analytics, and security events via the Dashboard. Set up alerting for issues or license expirations.
- Document and Train: Document configuration details, VLANs, IP schemes, and firewall policies for future reference. Provide access and training to other administrators as needed.
This structured method ensures rapid deployment, consistent policy enforcement, and maximum benefit from Cisco Meraki’s cloud-managed platform, whether deploying a single site or a distributed, multi-branch network.
Conclusion
Cisco Meraki security appliances offer a powerful combination of simplicity, scalability, and robust protection, all delivered through an intuitive cloud-managed platform. Throughout this blog post, we explored how Meraki streamlines network security—from its core components and versatile appliance models to its extensive network services and compliance-ready integrations.
Key takeaways include:
- Core technology built on a unified, cloud-first architecture enabling centralized management and real-time visibility.
- A range of appliance models designed to serve small branches, enterprise campuses, and cloud environments alike.
- Comprehensive network and security services such as stateful firewalls, SD-WAN, AMP, IDS/IPS, and traffic shaping—all built-in and easy to configure.
- Simplified licensing with all-inclusive support, firmware updates, and no surprise costs.
- Full alignment with industry compliance standards like HIPAA, PCI DSS, and GDPR, plus seamless integration with APIs, third-party tools, and Cisco’s broader security ecosystem.
- Guided deployment that makes it easy to roll out devices across multiple sites using zero-touch provisioning and intuitive setup steps.
Whether you’re securing a single branch office or building out a global network, Cisco Meraki delivers the flexibility and protection modern organizations need—without the complexity typically associated with enterprise-grade security.
Thanks for joining us on this deep dive into Cisco Meraki Security Appliances. We hope this guide helps you make informed decisions and bring simplicity, visibility, and peace of mind to your network operations. Until next time—stay secure and stay connected! 🚀