Table of Contents
- Overview
- Key VLAN Concepts
- VLAN Configuration CLI Quick Reference
- Supported VLAN Ranges
- Default VLAN Behavior on Cisco Switches
- Common VLAN Issues and Troubleshooting Tips
- Useful Cisco Documentation
- Conclusion
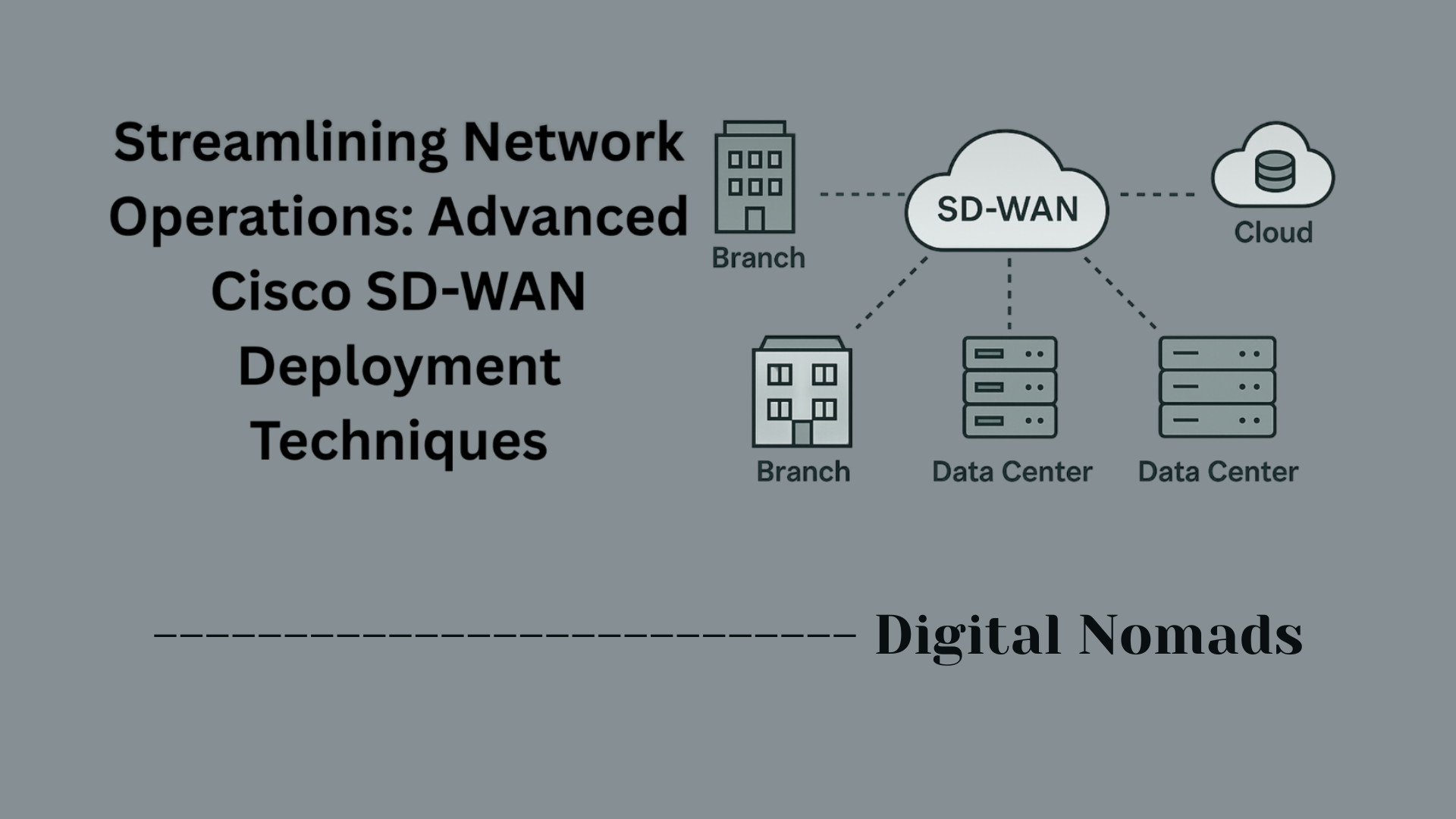
Cisco Switches: VLAN Support — Overview
What is VLAN Support on Cisco Switches?
VLAN support on Cisco switches refers to the ability of these devices to create, manage, and route Virtual Local Area Networks (VLANs) within an Ethernet network. A VLAN is a logical grouping of network devices and ports—regardless of their physical location—designed to segment a larger physical network into smaller, isolated broadcast domains. Cisco switches use VLANs to logically divide network traffic, offering improved security, scalability, and control within complex environments.
Why You Need to Know About VLANs
- Enhanced Security: VLANs isolate groups of users or devices, helping prevent unauthorized access and limiting the scope of broadcast storms. Sensitive data can be kept on separate VLANs, reducing exposure to threats and unauthorized access.
- Improved Network Performance: By dividing a network into smaller segments, VLANs reduce unnecessary traffic and the size of broadcast domains, improving overall efficiency and bandwidth utilization.
- Flexibility and Manageability: Network administrators can easily regroup users—regardless of their physical locations—by simply changing VLAN assignments, supporting moves, adds, and changes without physically rewiring the network.
- Simplified Troubleshooting and Maintenance: Network issues can be isolated to specific VLANs, making it easier to monitor and manage traffic, enforce policies, and apply updates or restrictions as needed.
How VLANs Work on Cisco Switches
- Logical Segmentation: VLANs are implemented by configuring switch ports with a unique VLAN ID. Each port can be set as either:
- Access Port: Carries traffic for a single VLAN, typically for end-user devices.
- Trunk Port: Carries traffic for multiple VLANs by tagging network frames, allowing switches and routers to interpret and separate the traffic accordingly.
- Traffic Isolation: Devices on the same VLAN communicate as if they were on the same physical network, even if connected to different switches. Devices on different VLANs cannot communicate directly unless permitted through routing or Layer 3 devices.
- VLAN Tagging: Cisco switches use the IEEE 802.1Q standard to add VLAN tags to Ethernet frames traversing trunk links. The tag indicates the VLAN membership, ensuring devices receive the correct network traffic.
- Centralized Control: VLANs can be managed manually on each switch, or centrally through protocols like VTP (VLAN Trunking Protocol), which propagates VLAN information throughout the network for consistency.
Key Takeaway
Cisco’s VLAN support is at the heart of designing secure, manageable, and scalable networks. Learning how VLANs operate, why they matter, and how Cisco switches implement them is essential for any network professional responsible for modern enterprise or campus environments. It lays the groundwork for organizational security, performance optimization, and future network expansion.
Key VLAN Concepts
Understanding key VLAN concepts is essential when working with Cisco switches, as VLANs help segment network traffic for improved security, performance, and manageability.
-
VLAN (Virtual Local Area Network):
A VLAN is a logical grouping of devices within a network, regardless of their physical location. VLANs segment the network into isolated broadcast domains, reducing traffic and improving security. -
Access Port:
An access port is a switch port assigned to a single VLAN. It carries only untagged traffic and is typically used to connect end-user devices like desktops or printers. -
Trunk Port:
A trunk port is a port that can carry traffic for multiple VLANs. It uses VLAN tagging (usually IEEE 802.1Q) to differentiate between VLANs. Trunks are often used to connect switches to other switches or to routers. -
VLAN Tagging:
VLAN tagging adds a header to Ethernet frames that include the VLAN ID. This helps switches understand which VLAN the traffic belongs to when sent over a trunk link. -
Native VLAN:
The native VLAN is the VLAN that carries untagged traffic on a trunk port. By default, Cisco switches use VLAN 1 as the native VLAN, but it is recommended to change it for security purposes. -
VLAN ID:
Each VLAN is uniquely identified by a VLAN ID ranging from 1 to 4094. VLAN IDs 1–1005 are standard, and 1006–4094 are extended VLANs. -
Broadcast Domain:
VLANs define the boundaries of a broadcast domain. Devices in the same VLAN can communicate directly with each other and share broadcast traffic.
VLAN Configuration CLI Quick Reference
This section provides a quick reference for essential VLAN configuration commands on Cisco switches, making it simple to set up, verify, and manage VLANs step by step.
-
Display Current VLANs:
show vlan brief
Use this command to quickly list all current VLANs and their associated ports. -
Create a VLAN:
vlan <VLAN_ID>
Enter VLAN configuration mode for the specified VLAN ID. -
Name the VLAN:
name <VLAN_NAME>
Assign a friendly name to the VLAN for easy identification. -
Assign Interface to VLAN (Access Port):
interface <INTERFACE_ID>
switchport mode access
switchport access vlan <VLAN_ID>
Set the interface as an access port and assign it to a VLAN. -
Configure Trunk Port:
interface <INTERFACE_ID>
switchport mode trunk
switchport trunk allowed vlan <VLAN_LIST>
Enable trunking and specify the list of VLANs allowed on the trunk. -
Set Native VLAN on Trunk:
switchport trunk native vlan <VLAN_ID>
Assign the native VLAN for untagged traffic on this trunk. -
Show Trunk Ports and Active VLANs:
show interfaces trunk
Display all trunk ports and their allowed and active VLANs.
| Command | Description |
|---|---|
show vlan brief |
Display currently configured VLANs |
vlan <VLAN_ID> |
Create a new VLAN with specified ID |
name <VLAN_NAME> |
Assign a name to the VLAN |
interface <INTERFACE_ID> |
Enter interface configuration mode |
switchport mode access |
Set interface as an access port |
switchport access vlan <VLAN_ID> |
Assign VLAN to access port |
switchport mode trunk |
Set interface as a trunk port |
switchport trunk allowed vlan <VLAN_LIST> |
Allow specified VLANs on trunk |
switchport trunk native vlan <VLAN_ID> |
Set the native VLAN for trunk |
show interfaces trunk |
Show trunk interfaces and their VLANs |
Tip: Always verify your configuration with show commands to ensure that VLANs and trunking settings are correctly applied.
Supported VLAN Ranges
This section outlines the VLAN ID ranges supported on Cisco switches and explains the distinctions between normal, extended, and reserved VLANs. Understanding these ranges is crucial for proper network segmentation and switch configuration.
-
VLAN ID Structure:
VLANs are identified by a unique VLAN ID, which is a number between 0 and 4095. However, not all IDs are available for user configuration.
- VLAN 0: Reserved for system use (802.1Q priority tagging).
- VLAN 1: Default VLAN for all switch ports out of the box—cannot be deleted[1][8].
- VLANs 2–1001: Normal-range VLANs (user-configurable for most networks).
- VLANs 1002–1005: Reserved for legacy technologies (FDDI/Token Ring)—automatically created and cannot be removed[1][8].
- VLANs 1006–4094: Extended-range VLANs, used for larger and more complex network environments. These require specific configuration modes on most switches[1][2][6].
- VLAN 4095: Reserved for system use, not available for configuration[1].
-
Normal vs. Extended VLANs:
- Normal Range: 1–1005
- Stored in the VLAN database (vlan.dat)
- Supported by all VTP versions
- Used in most business and enterprise networks - Extended Range: 1006–4094
- Stored in the switch running configuration (not vlan.dat)
- Requires VTP transparent mode for configuration in VTP v1/v2
- Needed by VTP version 3 for propagation
- Normal Range: 1–1005
-
Reserved VLANs:
Specific ranges including VLANs 0, 1002–1005, and 4095 are reserved and cannot be used for regular network segmentation[1][10].
| VLAN Range | Type | Description |
|---|---|---|
| 0 | Reserved | System use (priority tagging); not user-accessible |
| 1 | Normal (Default) | Default VLAN for all ports; cannot be deleted |
| 2–1001 | Normal | User-configurable for Ethernet VLANs |
| 1002–1005 | Reserved | Legacy FDDI/Token Ring VLANs; always present |
| 1006–4094 | Extended | User-configurable for large or service provider networks |
| 4095 | Reserved | System use only; not user-configurable |
Tip: When creating VLANs for production environments, avoid using the default and reserved VLAN IDs. For larger-scale segmentation, use extended VLANs with proper configuration settings as required by your Cisco device model.
Default VLAN Behavior on Cisco Switches
This section explains how Cisco switches handle VLANs by default, including the significance of VLAN 1, reserved VLANs, and best practices for configuring new environments.
-
Default VLAN Assignment:
Out of the box, all switch ports on a Cisco device are assigned to VLAN 1. This means that, unless specified otherwise, devices connected to the switch are on the same broadcast domain, allowing immediate communication[2][11]. -
VLAN 1 Behavior and Limitations:
- VLAN 1 is the default VLAN and cannot be deleted, suspended, or renamed.
- Many internal management and control protocols (like CDP, VTP, DTP, STP) use VLAN 1 by default for their traffic[17][18]. - VLAN 1 is also the default native VLAN for trunk ports, meaning untagged traffic on a trunk is assigned to VLAN 1 unless you specify a different VLAN as native[1][5]. -
Changing Port VLANs:
When you configure an access port to a different VLAN (e.g., VLAN 10), that port is no longer part of VLAN 1. Only unconfigured or default access ports remain in VLAN 1[2]. -
Reserved VLANs (1002–1005):
VLANs 1002–1005 are reserved for legacy technologies (FDDI/Token Ring) and cannot be deleted or used for standard Ethernet traffic[10][13]. These VLANs always appear in the VLAN table even if they are not actively used in modern networks. -
Best Practices:
- Cisco recommends not using VLAN 1 for management or user traffic due to security risks. Since VLAN 1 is widely known as the default, keeping critical systems on it can expose the network to certain vulnerabilities like VLAN hopping attacks[3][9]. - Assign unused ports to an unused VLAN and shut them down for security. - Always standardize the native VLAN on trunk links and avoid relying on the default settings, especially in production environments[5].
| VLAN | Purpose | Default Behavior |
|---|---|---|
| 1 | Default, Control/Management | All ports assigned by default; cannot delete or rename; default native VLAN |
| 1002–1005 | Reserved for Legacy (FDDI, Token Ring) | Cannot be deleted or used for Ethernet; always present in VLAN table |
| Custom (e.g., 10, 20, etc.) | User-Defined | Ports explicitly assigned; recommended for management and user data |
Tip: For improved security and management, always move user and management devices to a different VLAN, configure the native VLAN consistently across trunk links, and avoid using the default VLAN for any critical services.
Common VLAN Issues and Troubleshooting Tips
This section highlights frequently encountered VLAN problems on Cisco switches and offers practical, actionable troubleshooting steps to resolve them effectively.
-
VLAN Mismatch (Native VLAN Mismatch):
A native VLAN mismatch occurs when trunk links between two switches have different native VLANs configured. This can lead to connectivity issues and error messages.
Troubleshooting Steps:- Use
show interfaces trunkto check native VLANs on both ends. - Configure the same native VLAN on both trunk ports using
switchport trunk native vlan <VLAN_ID>[7][8][19].
- Use
-
Incorrect Port VLAN Assignment:
Devices fail to communicate if connected to ports assigned to the wrong VLAN or if ports are not correctly set as access or trunk.
Troubleshooting Steps:- Run
show vlanto verify port assignments and VLAN status. - Use
switchport access vlan <VLAN_ID>andswitchport mode accessto assign ports correctly[3][8].
- Run
-
Trunking Issues:
Trunk links may not pass VLAN traffic if not configured properly or if allowed VLAN lists are incomplete.
Troubleshooting Steps:- Check trunk port status and VLANs allowed with
show interfaces trunk. - Ensure all necessary VLANs are allowed using
switchport trunk allowed vlan <VLAN_LIST>.
- Check trunk port status and VLANs allowed with
-
VLAN Pruning and Spanning Tree Problems:
VLANs not forwarding because they have been pruned from trunks or blocked by Spanning Tree Protocol.
Troubleshooting Steps:- Confirm VLAN is not pruned unintentionally.
- Use
show spanning-tree vlan <VLAN_ID>to verify forwarding status[6].
-
Missing or Inactive VLANs:
A VLAN shows as "down" if no ports are assigned or if the VLAN does not exist on the switch.
Troubleshooting Steps:- Add the VLAN with
vlan <VLAN_ID>if missing. - Assign at least one port to the VLAN to activate it[5][11].
- Add the VLAN with
-
VTP and VLAN Propagation Issues:
VTP domain mismatches or misconfigurations can prevent VLANs from being learned or propagated.
Troubleshooting Steps:- Ensure switches are in the same VTP domain and version.
- Verify VTP mode and configuration with
show vtp status[14].
-
Voice VLAN Misconfiguration:
Phones and PCs not working as expected if the voice VLAN is missing or incorrectly set.
Troubleshooting Steps:- Confirm voice VLAN with
show run interface <INTERFACE_ID>and proper VLAN configuration for phone and data[6].
- Confirm voice VLAN with
| Issue | Symptoms | Key Commands | Resolution |
|---|---|---|---|
| Native VLAN mismatch | CDP error messages, lost connectivity | show interfaces trunk |
Match native VLANs on both trunk ends[7][8][19] |
| Incorrect port VLAN | Devices can’t talk, wrong broadcast domain | show vlan |
Assign correct VLAN, set mode access[3][8] |
| Trunk allowed VLAN | VLAN does not traverse trunk | show interfaces trunk |
Allow required VLANs on trunk |
| Missing VLAN | Ports inactive, VLAN “down” status | show vlan |
Create VLAN, assign ports[5][11] |
| VTP/Propagation | VLANs missing on some switches | show vtp status |
Fix VTP domain/version/config[14] |
| Voice VLAN | IP phones not working | show run interface |
Set/access correct voice VLAN[6] |
Tip: Begin troubleshooting by checking physical connectivity, then verify VLAN and trunk configurations. Many VLAN issues stem from simple misconfigurations that are easy to overlook!
Useful Cisco Documentation
This section highlights trusted Cisco resources and official documentation that are invaluable for configuring, troubleshooting, and deepening your understanding of VLANs on Cisco switches. Use these references to ensure your knowledge remains current and aligned with best practices.
-
Cisco Catalyst Switches: VLAN Configuration Guide:
Step-by-step procedures for VLAN setup, trunking, verification, and best practices on Catalyst series switches.
Ideal for beginners and experienced network engineers alike to get the most out of VLAN features. -
Cisco Networking Academy: VLAN Implementation Module:
Comprehensive learning module on VLAN concepts, configuration commands, security implications, and troubleshooting.
Best for visual learners seeking guided tutorials and hands-on labs. -
Cisco Official Command References:
Detailed syntax and usage notes for all CLI commands, including examples related to VLAN management.
Perfect for quick look-ups during deployment or troubleshooting sessions. -
Cisco TechDocs: Best Practices for VLAN Security:
Reviews the risks of default settings, native VLAN exploits, and offers actionable guidance for securing VLAN environments.
Essential reading for network administrators focused on maintaining a secure architecture. -
Cisco Community Forums and Support:
A vibrant place to discuss real-world issues, ask questions, and review peer solutions on VLAN topics from other IT professionals.
| Resource | Description | Recommended For |
|---|---|---|
| Catalyst VLAN Configuration Guide | Procedures, CLI, and best practices for VLANs on Cisco Catalyst series | Beginners, Pros, Troubleshooting |
| Networking Academy VLAN Module | Tutorials, labs, and visual explanations of VLAN concepts and setup | Learners, Instructors |
| Official Command References | Comprehensive list and syntax for VLAN-related CLI commands | Day-to-Day Admin, Quick Look-Up |
| TechDocs VLAN Security | VLAN security threats, mitigation strategies, and design best practices | Security Admins, Architects |
| Cisco Community Forums | Community Q&A, troubleshooting stories, and peer advice | All Users |
Tip: Bookmark these resources so you can quickly access authoritative guides and answers for your VLAN deployments, troubleshooting, and design questions.
Conclusion
Throughout this blog post, we’ve explored how Cisco switches provide robust VLAN support to help design scalable, secure, and efficient network architectures. Here's a quick recap of what we've covered:
- Key VLAN Concepts: VLANs logically segment traffic across networks. Access ports handle traffic for one VLAN, while trunk ports carry multiple VLANs using tagging standards like 802.1Q.
- VLAN Configuration CLI Quick Reference: We walked through essential Cisco CLI commands that make creating, assigning, and troubleshooting VLANs straightforward.
- Supported VLAN Ranges: Cisco switches organize VLANs into normal (1–1005), extended (1006–4094), and reserved ranges, all of which serve different use cases and require different configuration approaches.
- Default VLAN Behavior: VLAN 1 is the default VLAN used out-of-the-box, but best practice is to configure user and management traffic on alternate VLANs for improved security and control.
- Common VLAN Issues and Troubleshooting Tips: From native VLAN mismatches to trunk configuration errors and missing VLANs, we learned how to identify and resolve common VLAN-related problems effectively.
- Useful Cisco Documentation: We wrapped up with a curated list of official Cisco resources, guides, and learning tools to support you during hands-on configuration and learning.
No matter your experience level, understanding VLANs is essential to managing a strong, clean, and secure Layer 2 environment. VLANs help keep your traffic organized, improve broadcast efficiency, and form the foundation of virtually every modern switched network.
👋 Thanks for reading!
We hope this guide gave you both insight and confidence when it comes to working with VLANs on Cisco switches. Whether you're configuring your first VLAN or fine-tuning a production network, keep referring back to these steps and tips to stay on the right track.
Stay connected, stay segmented—and happy switching! 😊